DMVPN FlexVPN 实验
网络拓结构为下图:
每个节点中lo接口均为了模拟内部网段,SPOKE-03是为了模拟FlexVPN在经过NAT以后是否可以正常通信。所以在DMVPN章节不会涉及该节点的配置。

基础配置:
- HUB-CA
## 配置时间
service timestamps debug datetime localtime show-timezone
service timestamps log datetime localtime show-timezone
clock timezone GMT 8 0
## 充当NTP server
ntp master 1
hostname Hub-CA
ip domain name cisco.com
interface Loopback0
ip address 192.168.10.1 255.255.255.0
!
interface Ethernet0/0
ip address 123.1.1.10 255.255.255.0
- Spoke-01
service timestamps debug datetime localtime show-timezone
service timestamps log datetime localtime show-timezone
clock timezone CST 8 0
hostname Spoke-01
ip domain name cisco.com
interface Loopback0
ip address 192.168.1.1 255.255.255.0
!
interface Ethernet0/0
ip address 123.1.1.1 255.255.255.0
ntp server 123.1.1.10
- Spoke-02
service timestamps debug datetime localtime show-timezone
service timestamps log datetime localtime show-timezone
clock timezone CST 8 0
hostname Spoke-02
ip domain name cisco.com
interface Loopback0
ip address 192.168.2.1 255.255.255.0
!
interface Ethernet0/0
ip address 123.1.1.2 255.255.255.0
ntp server 123.1.1.10
- Internet-Route
service timestamps debug datetime localtime show-timezone
service timestamps log datetime localtime show-timezone
clock timezone CST 8 0
hostname Internet-Route
interface Ethernet0/0
ip address 123.1.1.3 255.255.255.0
ip nat outside
ip virtual-reassembly in
!
interface Ethernet0/1
ip address 172.16.168.1 255.255.255.0
ip nat inside
ip virtual-reassembly in
ip nat inside source list local_nat interface Ethernet0/0 overload
ip access-list extended local_nat
permit ip any any
ntp server 123.1.1.10
- Spoke-03
service timestamps debug datetime localtime show-timezone
service timestamps log datetime localtime show-timezone
hostname Spoke-03
clock timezone CST 8 0
ip domain name cisco.com
interface Loopback0
ip address 192.168.3.1 255.255.255.0
!
interface Ethernet0/0
ip address 172.16.168.2 255.255.255.0
ip route 0.0.0.0 0.0.0.0 172.16.168.1
ntp server 123.1.1.10
DMVPN PKI 认证实验
DMVPN 使用第三方证书服务器
HUB路由器
该部分需要安装证书服务器。(这部分内容请参考百度、Google)
- 下载CA证书用记事本打开,出现根证书字符串
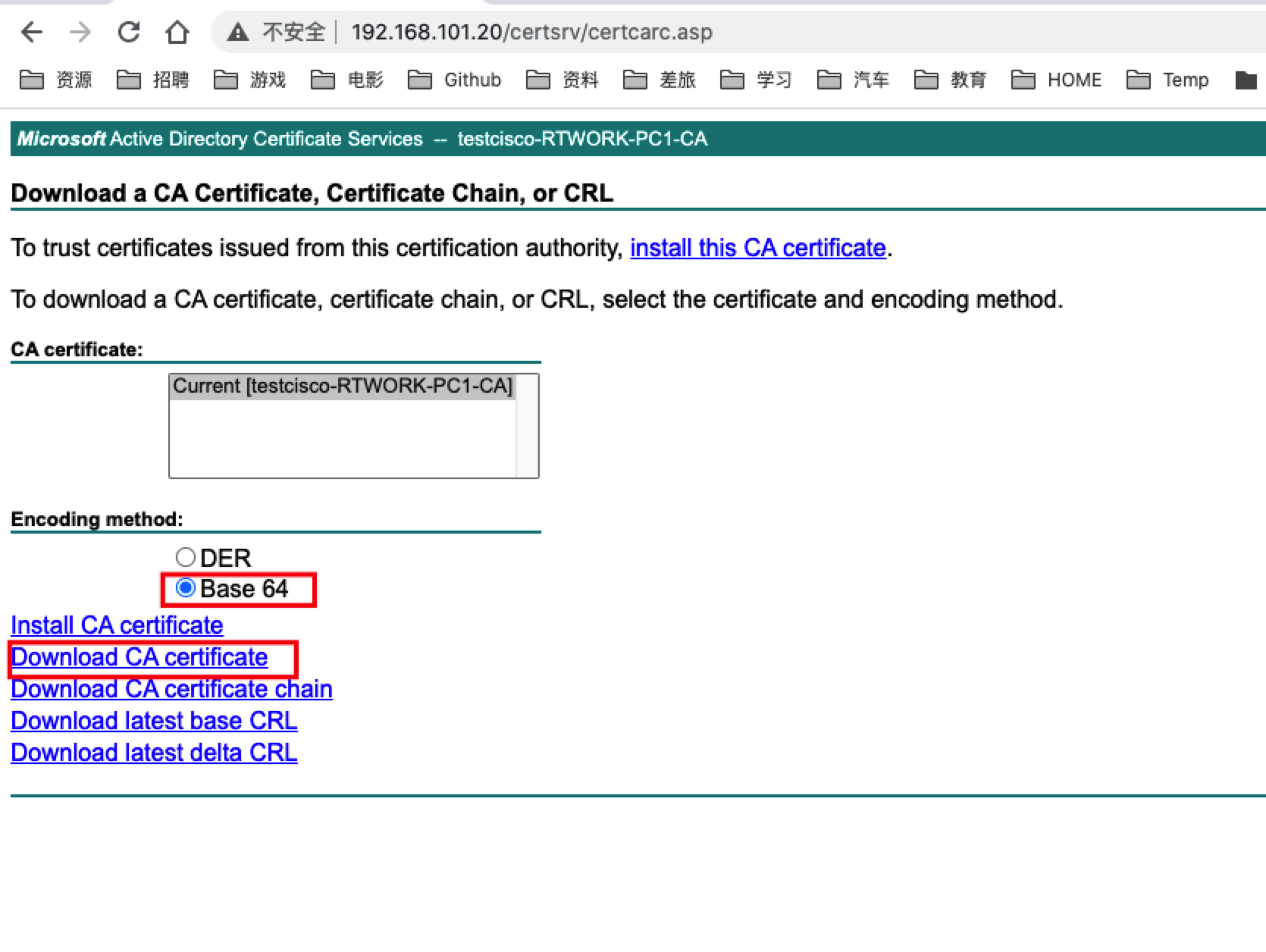
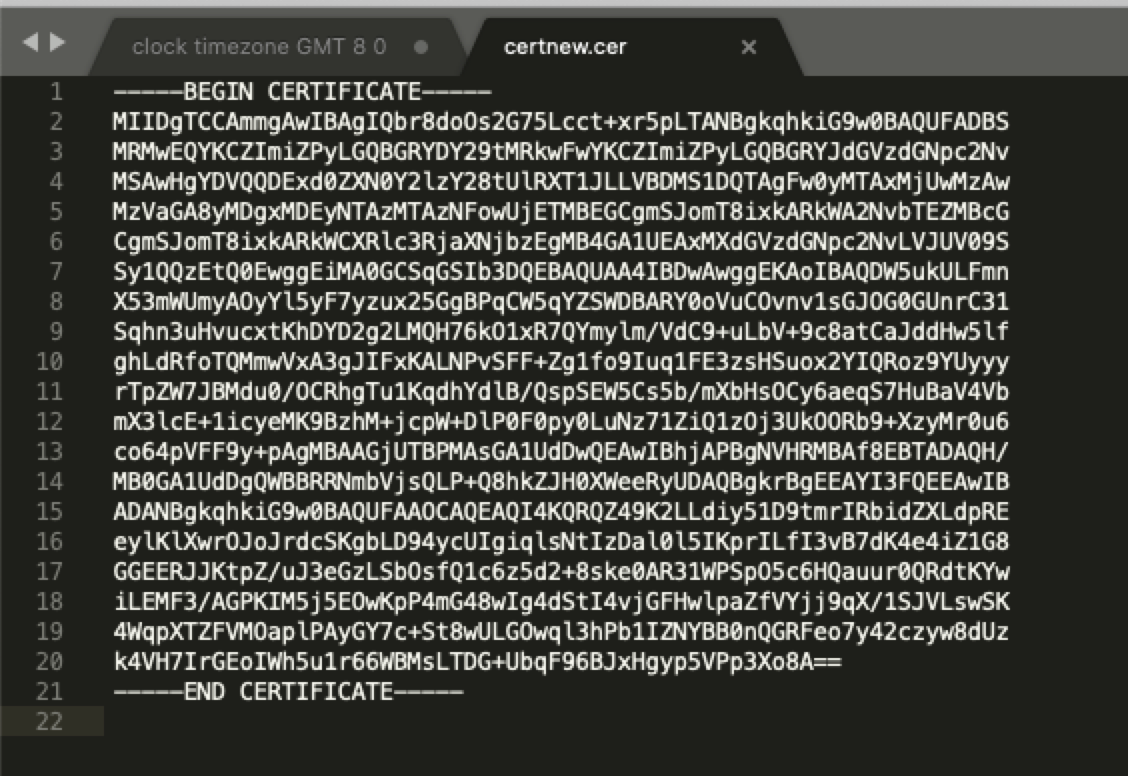
- 配置CISCO路由器导入根证 书,命令如下:
Hub-CA(config)#crypto key generate rsa modulus 2048 label hub-key # 需要先产生密钥对
The name for the keys will be: hub-key
% The key modulus size is 2048 bits
% Generating 2048 bit RSA keys, keys will be non-exportable...
[OK] (elapsed time was 1 seconds)
Hub-CA(config)#crypto pki trustpoint testca # 定义CA证书名称
Hub-CA(ca-trustpoint)#enrollment terminal # 定义证书获得方式,手动导入
Hub-CA(ca-trustpoint)#subject-name cn=Hub-CA,dc=testcisco,dc=com
Hub-CA(ca-trustpoint)#revocation-check none # 不检查证书是否吊销
Hub-CA(ca-trustpoint)#rsakeypair hub-key # 调用密钥对
# 使用命令crypto pki authenticate testca,导入testca的根证书
Hub-CA(config)#crypto pki authenticate testca
Enter the base 64 encoded CA certificate.
End with a blank line or the word "quit" on a line by itself
-----BEGIN CERTIFICATE-----
MIIDgTCCAmmgAwIBAgIQbr8doOs2G75Lcct+xr5pLTANBgkqhkiG9w0BAQUFADBS
MRMwEQYKCZImiZPyLGQBGRYDY29tMRkwFwYKCZImiZPyLGQBGRYJdGVzdGNpc2Nv
MSAwHgYDVQQDExd0ZXN0Y2lzY28tUlRXT1JLLVBDMS1DQTAgFw0yMTAxMjUwMzAw
MzVaGA8yMDgxMDEyNTAzMTAzNFowUjETMBEGCgmSJomT8ixkARkWA2NvbTEZMBcG
CgmSJomT8ixkARkWCXRlc3RjaXNjbzEgMB4GA1UEAxMXdGVzdGNpc2NvLVJUV09S
Sy1QQzEtQ0EwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDW5ukULFmn
X53mWUmyAOyYl5yF7yzux25GgBPqCW5qYZSWDBARY0oVuCOvnv1sGJOG0GUnrC31
Sqhn3uHvucxtKhDYD2g2LMQH76kO1xR7QYmylm/VdC9+uLbV+9c8atCaJddHw5lf
ghLdRfoTQMmwVxA3gJIFxKALNPvSFF+Zg1fo9Iuq1FE3zsHSuox2YIQRoz9YUyyy
rTpZW7JBMdu0/OCRhgTu1KqdhYdlB/QspSEW5Cs5b/mXbHsOCy6aeqS7HuBaV4Vb
mX3lcE+1icyeMK9BzhM+jcpW+DlP0F0py0LuNz71ZiQ1zOj3UkOORb9+XzyMr0u6
co64pVFF9y+pAgMBAAGjUTBPMAsGA1UdDwQEAwIBhjAPBgNVHRMBAf8EBTADAQH/
MB0GA1UdDgQWBBRRNmbVjsQLP+Q8hkZJH0XWeeRyUDAQBgkrBgEEAYI3FQEEAwIB
ADANBgkqhkiG9w0BAQUFAAOCAQEAQI4KQRQZ49K2LLdiy51D9tmrIRbidZXLdpRE
eylKlXwrOJoJrdcSKgbLD94ycUIgiqlsNtIzDal0l5IKprILfI3vB7dK4e4iZ1G8
GGEERJJKtpZ/uJ3eGzLSbOsfQ1c6z5d2+8ske0AR31WPSpO5c6HQauur0QRdtKYw
iLEMF3/AGPKIM5j5EOwKpP4mG48wIg4dStI4vjGFHwlpaZfVYjj9qX/1SJVLswSK
4WqpXTZFVMOaplPAyGY7c+St8wULGOwql3hPb1IZNYBB0nQGRFeo7y42czyw8dUz
k4VH7IrGEoIWh5u1r66WBMsLTDG+UbqF96BJxHgyp5VPp3Xo8A==
-----END CERTIFICATE-----
quit
# 并用quit命令退出根证书,退出后系统会弹出对话框,询问是否接受证书
Certificate has the following attributes:
Fingerprint MD5: 25A595E5 3F591617 B82E80E1 16686B51
Fingerprint SHA1: 1F28E4B2 BF190E40 453169E4 21D1C4AD 45897B54
% Do you accept this certificate? [yes/no]: yes # 输入yes接受证书。
Trustpoint CA certificate accepted.
% Certificate successfully imported
- 在路由器生成证书申请请求
路由器会询问是否带设备序列号和IP地址,是否再次查看信息。需要复制字符串。 申请CA证书。将此字符串复制下来,相关机构的负责人会根据此字符串再次生成一 个准入证书。
Hub-CA(config)#crypto pki enroll testca
% Start certificate enrollment ..
% The subject name in the certificate will include: cn=Hub-CA,dc=testcisco,dc=com
% The subject name in the certificate will include: Hub-CA.cisco.com
% Include the router serial number in the subject name? [yes/no]: no
% Include an IP address in the subject name? [no]: no
Display Certificate Request to terminal? [yes/no]: yes
Certificate Request follows:
MIICyDCCAbACAQAwYjETMBEGCgmSJomT8ixkARkWA2NvbTEZMBcGCgmSJomT8ixk
ARkWCXRlc3RjaXNjbzEPMA0GA1UEAxMGSHViLUNBMR8wHQYJKoZIhvcNAQkCFhBI
dWItQ0EuY2lzY28uY29tMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA
rENDxxCEJatqpZsBf2K/drbHjAUXoz38a/xWuneOfW3pTj6NEH4cIvU490/kACQB
qVQKWxS4RPBUwGafG/jUIgZMMui5WX5sSaKf//xZi05T48nW4Ni2nhlK9iSn7NDU
TlRK/ckymNI/KA9ItarzCRW78uo84eRit1UFcuy+5ZBiIYY0HSfiQHToaYIoO/TB
pv8VdAwzNTzmlwfhz8n2ri+DFKv7WGwL4C80XWAr2txmlfT7gVVGIBFMLQgI6r29
TXIkGgEYlO1R3/npvlTJg1Q4hsZFlaFfOyla0nT/qcGcjn28mQaeshuAfoA322rE
1QsYxkY42e6umGh68CPogQIDAQABoCEwHwYJKoZIhvcNAQkOMRIwEDAOBgNVHQ8B
Af8EBAMCBaAwDQYJKoZIhvcNAQEFBQADggEBAJQVTeVaKKHuY43E96AO35yFoBs2
nuQfgICmLj/YH+PuSGek0iRtFk6SrjrWl/6V4qentg5aEiyyNeHph/YtRFIW0pHT
oYBM0ZIjsmxx8wph+4BWIxkzlcerAoyMTiKXat9pzaqwhoo0G3+U6Il7aOS4ab7x
BSM3tbQ/U7u4zhB+gDke7UHxAdPIz2WHbq7T4kAC/R6roMJccEKqMl0x9fsOnO2t
ecZMBqLIc943TFQ2sEW8MYYUb91Ajiro0gVj66mmIHaE8gk78uBfKXMa1nk+KqEq
nJmL9mBbMw+ujmfO9hVod+/xWA/IomMTgrKzWVGaD2jA1n9aH0eSXk+oXt0=
---End - This line not part of the certificate request---
Redisplay enrollment request? [yes/no]: no
- 向证书服务器提交申请,并使用文本方式打开证书。
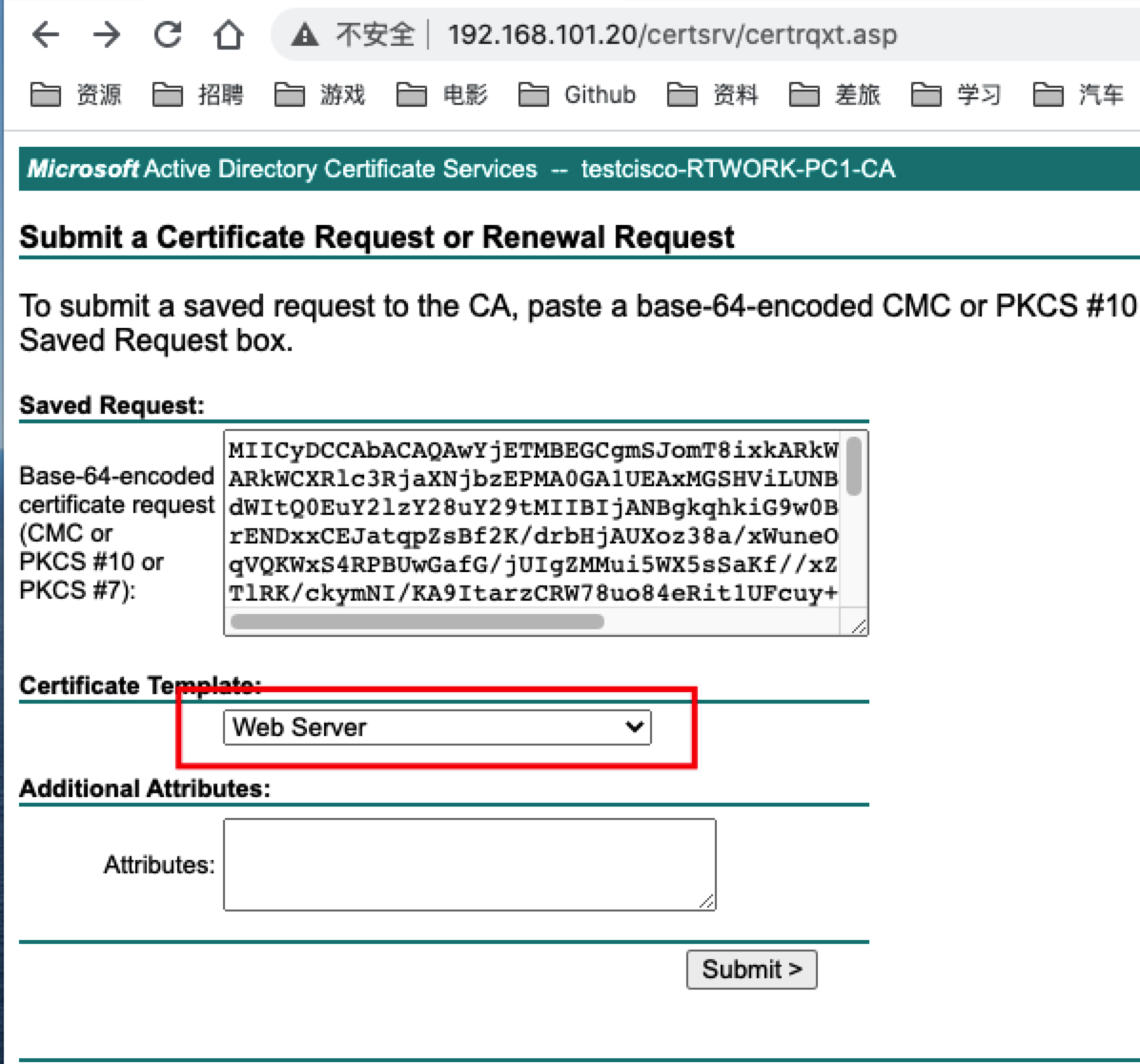
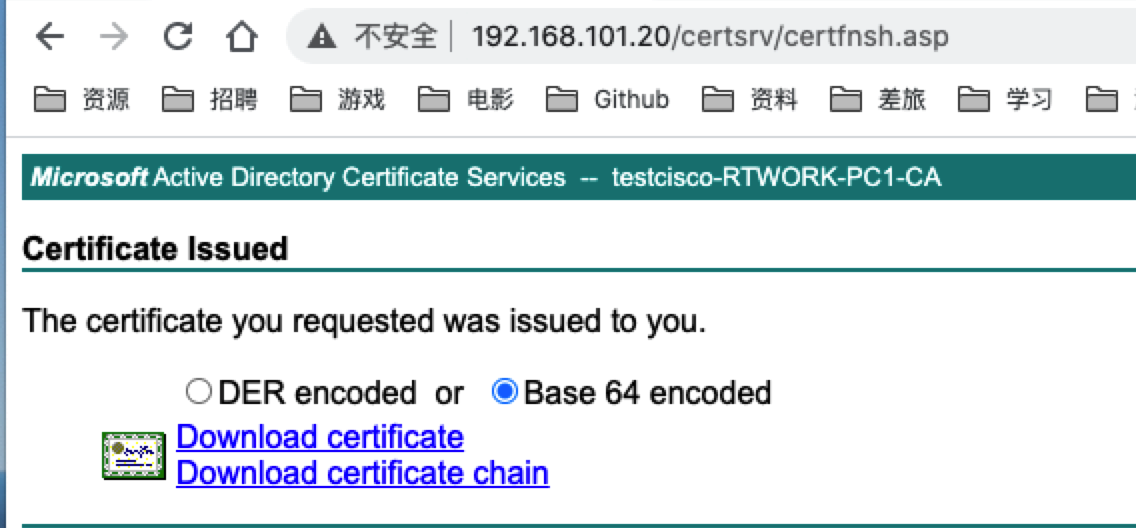
- 路由器导入申请的证书
Hub-CA(config)#crypto pki import testca certificate # 导入证书
Enter the base 64 encoded certificate.
End with a blank line or the word "quit" on a line by itself
-----BEGIN CERTIFICATE-----
MIIFWTCCBEGgAwIBAgITMQAAAAiMbmt7xdFeWAAAAAAACDANBgkqhkiG9w0BAQUF
ADBSMRMwEQYKCZImiZPyLGQBGRYDY29tMRkwFwYKCZImiZPyLGQBGRYJdGVzdGNp
c2NvMSAwHgYDVQQDExd0ZXN0Y2lzY28tUlRXT1JLLVBDMS1DQTAeFw0yMTAxMjUw
NzEwMDBaFw0yMzAxMjUwNzEwMDBaMEExEzARBgoJkiaJk/IsZAEZFgNjb20xGTAX
BgoJkiaJk/IsZAEZFgl0ZXN0Y2lzY28xDzANBgNVBAMTBkh1Yi1DQTCCASIwDQYJ
KoZIhvcNAQEBBQADggEPADCCAQoCggEBAKxDQ8cQhCWraqWbAX9iv3a2x4wFF6M9
/Gv8Vrp3jn1t6U4+jRB+HCL1OPdP5AAkAalUClsUuETwVMBmnxv41CIGTDLouVl+
bEmin//8WYtOU+PJ1uDYtp4ZSvYkp+zQ1E5USv3JMpjSPygPSLWq8wkVu/LqPOHk
YrdVBXLsvuWQYiGGNB0n4kB06GmCKDv0wab/FXQMMzU85pcH4c/J9q4vgxSr+1hs
C+AvNF1gK9rcZpX0+4FVRiARTC0ICOq9vU1yJBoBGJTtUd/56b5UyYNUOIbGRZWh
XzspWtJ0/6nBnI59vJkGnrIbgH6AN9tqxNULGMZGONnurphoevAj6IECAwEAAaOC
AjcwggIzMA4GA1UdDwEB/wQEAwIFoDAdBgNVHQ4EFgQUWhdrFm4JGJfVBSUfl3KP
FXzjThMwHwYDVR0jBBgwFoAUUTZm1Y7ECz/kPIZGSR9F1nnkclAwgdoGA1UdHwSB
0jCBzzCBzKCByaCBxoaBw2xkYXA6Ly8vQ049dGVzdGNpc2NvLVJUV09SSy1QQzEt
Q0EsQ049cnR3b3JrLXBjMSxDTj1DRFAsQ049UHVibGljJTIwS2V5JTIwU2Vydmlj
ZXMsQ049U2VydmljZXMsQ049Q29uZmlndXJhdGlvbixEQz10ZXN0Y2lzY28sREM9
Y29tP2NlcnRpZmljYXRlUmV2b2NhdGlvbkxpc3Q/YmFzZT9vYmplY3RDbGFzcz1j
UkxEaXN0cmlidXRpb25Qb2ludDCBywYIKwYBBQUHAQEEgb4wgbswgbgGCCsGAQUF
BzAChoGrbGRhcDovLy9DTj10ZXN0Y2lzY28tUlRXT1JLLVBDMS1DQSxDTj1BSUEs
Q049UHVibGljJTIwS2V5JTIwU2VydmljZXMsQ049U2VydmljZXMsQ049Q29uZmln
dXJhdGlvbixEQz10ZXN0Y2lzY28sREM9Y29tP2NBQ2VydGlmaWNhdGU/YmFzZT9v
YmplY3RDbGFzcz1jZXJ0aWZpY2F0aW9uQXV0aG9yaXR5MCEGCSsGAQQBgjcUAgQU
HhIAVwBlAGIAUwBlAHIAdgBlAHIwEwYDVR0lBAwwCgYIKwYBBQUHAwEwDQYJKoZI
hvcNAQEFBQADggEBAIiVkYtVl2EWSIY+GZTuxY/zb4R/8Pa1dU8K5hcHlUxQTKD2
ruNAuFcDTcJziGmQqgdr+viK3puhd//ePWH6TNgQi3x9lwSyUwxbmb2PiNsbKQGn
vgXo4yLL4Elc2V9Ebh4kbH6aseFXiBluJM5rbp0nAgbztQbl6fAhHNMr0iTyWv2x
562LOE3zNiOEVLeR9GuI/tAD0WTnezMAsxh0ev/9Lh5h3NknG8MNyRPy7cTBbnop
2eT5+zV1Qk8aaAOhv0rnVP/D9oY6Fv/d9KxIiZ9bMMBe+OBvAvAF5cj/W8PmkYaA
ZJvHTQBLsGHfodaVC+xO4W3nfZ9ffVarJDKr54A=
-----END CERTIFICATE-----
quit
% Router Certificate successfully imported
Hub-CA#show crypto pki certificates # 查看证书
Certificate
Status: Available
Certificate Serial Number (hex): 31000000088C6E6B7BC5D15E58000000000008
Certificate Usage: General Purpose
Issuer:
cn=testcisco-RTWORK-PC1-CA
dc=testcisco
dc=com
Subject:
Name: Hub-CA
cn=Hub-CA
dc=testcisco
dc=com
CRL Distribution Points:
ldap:///CN=testcisco-RTWORK-PC1-CA,CN=rtwork-pc1,CN=CDP,CN=Public%20Key%20Services,CN=Services,CN=Configuration,DC=testcisco,DC=com?certificateRevocationList?base?objectClass=cRLDistributionPoint
Validity Date:
start date: 15:10:00 GMT Jan 25 2021
end date: 15:10:00 GMT Jan 25 2023
Associated Trustpoints: testca
CA Certificate
Status: Available
Certificate Serial Number (hex): 6EBF1DA0EB361BBE4B71CB7EC6BE692D
Certificate Usage: Signature
Issuer:
cn=testcisco-RTWORK-PC1-CA
dc=testcisco
dc=com
Subject:
cn=testcisco-RTWORK-PC1-CA
dc=testcisco
dc=com
Validity Date:
start date: 11:00:35 GMT Jan 25 2021
end date: 04:42:18 GMT Dec 20 1944
Associated Trustpoints: testca
- 配置DMVPN环境
crypto isakmp enable
crypto isakmp policy 10
encr aes
hash sha256
authentication rsa-sig
lifetime 86400
group 2
crypto isakmp invalid-spi-recovery
crypto isakmp keepalive 30 10 periodic
crypto isakmp nat keepalive 360
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association replay disable
crypto ipsec transform-set 3DES esp-3des esp-sha-hmac
mode transport
crypto ipsec nat-transparency spi-matching
crypto ipsec profile NEPROF-MKT
set transform-set 3DES
set pfs group2
interface Tunnel20
description DMVPN-HUB
bandwidth 1000000
ip address 10.16.1.10 255.255.255.0
no ip redirects
ip mtu 1400
ip nhrp authentication cisco
ip nhrp map multicast dynamic
ip nhrp network-id 20
ip nhrp holdtime 300
ip tcp adjust-mss 1360
ip ospf network broadcast
ip ospf priority 95
ip ospf cost 2000
load-interval 30
delay 1000
tunnel source Ethernet0/0
tunnel mode gre multipoint
tunnel key 20
tunnel path-mtu-discovery
tunnel bandwidth transmit 100000
tunnel bandwidth receive 100000
tunnel protection ipsec profile NEPROF-MKT
- 配置OSPF环境
interface Loopback0
ip address 192.168.10.1 255.255.255.0
ip ospf network point-to-point
ip ospf 100 area 10
router ospf 100
network 10.16.1.0 0.0.0.255 area 0
Spoke-01
证书的申请和导入详细部分请参考HUB配置,这里只做简单阐述和标记变动的地方。
- 导入CA证书并信任
Spoke-01(config)#crypto key generate rsa modulus 2048 label spoke01-key # 需要先产生密钥对
Spoke-01(config)#crypto pki trustpoint testca # 定义CA证书名称
Spoke-01(ca-trustpoint)#enrollment terminal # 定义证书获得方式,手动导入
Spoke-01(ca-trustpoint)#subject-name cn=spoke01,dc=testcisco,dc=com
Spoke-01(ca-trustpoint)#revocation-check none # 不检查证书是否吊销
Spoke-01(ca-trustpoint)#rsakeypair spoke01-key # 调用密钥对
# 使用命令crypto pki authenticate testca,导入testca的根证书
Spoke-01(config)#crypto pki authenticate testca
Enter the base 64 encoded CA certificate.
End with a blank line or the word "quit" on a line by itself
-----BEGIN CERTIFICATE-----
MIIDgTCCAmmgAwIBAgIQbr8doOs2G75Lcct+xr5pLTANBgkqhkiG9w0BAQUFADBS
MRMwEQYKCZImiZPyLGQBGRYDY29tMRkwFwYKCZImiZPyLGQBGRYJdGVzdGNpc2Nv
MSAwHgYDVQQDExd0ZXN0Y2lzY28tUlRXT1JLLVBDMS1DQTAgFw0yMTAxMjUwMzAw
MzVaGA8yMDgxMDEyNTAzMTAzNFowUjETMBEGCgmSJomT8ixkARkWA2NvbTEZMBcG
CgmSJomT8ixkARkWCXRlc3RjaXNjbzEgMB4GA1UEAxMXdGVzdGNpc2NvLVJUV09S
Sy1QQzEtQ0EwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDW5ukULFmn
X53mWUmyAOyYl5yF7yzux25GgBPqCW5qYZSWDBARY0oVuCOvnv1sGJOG0GUnrC31
Sqhn3uHvucxtKhDYD2g2LMQH76kO1xR7QYmylm/VdC9+uLbV+9c8atCaJddHw5lf
ghLdRfoTQMmwVxA3gJIFxKALNPvSFF+Zg1fo9Iuq1FE3zsHSuox2YIQRoz9YUyyy
rTpZW7JBMdu0/OCRhgTu1KqdhYdlB/QspSEW5Cs5b/mXbHsOCy6aeqS7HuBaV4Vb
mX3lcE+1icyeMK9BzhM+jcpW+DlP0F0py0LuNz71ZiQ1zOj3UkOORb9+XzyMr0u6
co64pVFF9y+pAgMBAAGjUTBPMAsGA1UdDwQEAwIBhjAPBgNVHRMBAf8EBTADAQH/
MB0GA1UdDgQWBBRRNmbVjsQLP+Q8hkZJH0XWeeRyUDAQBgkrBgEEAYI3FQEEAwIB
ADANBgkqhkiG9w0BAQUFAAOCAQEAQI4KQRQZ49K2LLdiy51D9tmrIRbidZXLdpRE
eylKlXwrOJoJrdcSKgbLD94ycUIgiqlsNtIzDal0l5IKprILfI3vB7dK4e4iZ1G8
GGEERJJKtpZ/uJ3eGzLSbOsfQ1c6z5d2+8ske0AR31WPSpO5c6HQauur0QRdtKYw
iLEMF3/AGPKIM5j5EOwKpP4mG48wIg4dStI4vjGFHwlpaZfVYjj9qX/1SJVLswSK
4WqpXTZFVMOaplPAyGY7c+St8wULGOwql3hPb1IZNYBB0nQGRFeo7y42czyw8dUz
k4VH7IrGEoIWh5u1r66WBMsLTDG+UbqF96BJxHgyp5VPp3Xo8A==
-----END CERTIFICATE-----
quit
# 并用quit命令退出根证书,退出后系统会弹出对话框,询问是否接受证书
Certificate has the following attributes:
Fingerprint MD5: 25A595E5 3F591617 B82E80E1 16686B51
Fingerprint SHA1: 1F28E4B2 BF190E40 453169E4 21D1C4AD 45897B54
% Do you accept this certificate? [yes/no]: yes # 输入yes接受证书。
Trustpoint CA certificate accepted.
% Certificate successfully imported
- 申请路由器证书并导入
Spoke-01(config)#crypto pki enroll testca # 创建证书请求
% Start certificate enrollment ..
% The subject name in the certificate will include: cn=spoke01,dc=testcisco,dc=com
% The subject name in the certificate will include: Spoke-01.cisco.com
% Include the router serial number in the subject name? [yes/no]: no
% Include an IP address in the subject name? [no]: no
Display Certificate Request to terminal? [yes/no]: yes
Certificate Request follows:
MIICyzCCAbMCAQAwZTETMBEGCgmSJomT8ixkARkWA2NvbTEZMBcGCgmSJomT8ixk
ARkWCXRlc3RjaXNjbzEQMA4GA1UEAxMHc3Bva2UwMTEhMB8GCSqGSIb3DQEJAhYS
U3Bva2UtMDEuY2lzY28uY29tMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKC
AQEAmTt6lv2eIuUY9CCxAgC56v25Rm2aTF1jjZ2Ij7S9AFQwXd9p9NRitVrlNhA4
ZwaUq63BVo0CqyY88EzSfe2tZ9PCXzqhZW+IzHS3LkAM7R8TMR1P+E07ENbvhucC
geu3547BUtQ9D4J6CEMnqS4LzKaDUEmics2dO+01ZYCS6aB12irb6x9RyAFK+pZl
N0prty6XIOaU1i5EpIU5nA2AlMSawZiWU8n8+jIlYXiNY9+JT8ioe8K/HJmpclJI
wVPXZplLNG3/eR3okYRBPxch2mkAKc76j0MwjTpHNQ6L7X1mVxLYenKT3pwsPTYT
fu7wbRRo6OS2Rdh+Q8YqtinuNQIDAQABoCEwHwYJKoZIhvcNAQkOMRIwEDAOBgNV
HQ8BAf8EBAMCBaAwDQYJKoZIhvcNAQEFBQADggEBAEkiS2LZHqlvhsLLBv9kewKf
LweZ3/gY2SOIQWbVQA+xNvYJPNQ564oMZzZ0Lz2vjySJD7JdY1wBXf8gTQIjV4rY
o1bJK5DgOEMRi2BGeoYfcjpcFMJBfqEIMTiVdKduw7e54TXR/RHzIhHLyOBqs/Lg
u/5Iq3u/Wo7ERMs2puLbITDsW6fq5B/OPmEtvXVcy4u+HDsQQat0gTHZY9O387sc
MrYwWEf0DMGZOxMbn/fgGMwx5u1+pDap+iHq272JBKl33HVAaWaW6zY1SUHULGqY
/y1UsZFRwiYTqMwEov9uXww5T32sGofDjNC2xefdDGIYfppK/sai1hay54QWDZk=
---End - This line not part of the certificate request---
Redisplay enrollment request? [yes/no]: no
Spoke-01(config)#crypto pki import testca certificate # 导入证书
Enter the base 64 encoded certificate.
End with a blank line or the word "quit" on a line by itself
-----BEGIN CERTIFICATE-----
MIIFWjCCBEKgAwIBAgITMQAAAAq5o70V/R63WQAAAAAACjANBgkqhkiG9w0BAQUF
ADBSMRMwEQYKCZImiZPyLGQBGRYDY29tMRkwFwYKCZImiZPyLGQBGRYJdGVzdGNp
c2NvMSAwHgYDVQQDExd0ZXN0Y2lzY28tUlRXT1JLLVBDMS1DQTAeFw0yMTAxMjUw
NzQzNDhaFw0yMzAxMjUwNzQzNDhaMEIxEzARBgoJkiaJk/IsZAEZFgNjb20xGTAX
BgoJkiaJk/IsZAEZFgl0ZXN0Y2lzY28xEDAOBgNVBAMTB3Nwb2tlMDEwggEiMA0G
CSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCZO3qW/Z4i5Rj0ILECALnq/blGbZpM
XWONnYiPtL0AVDBd32n01GK1WuU2EDhnBpSrrcFWjQKrJjzwTNJ97a1n08JfOqFl
b4jMdLcuQAztHxMxHU/4TTsQ1u+G5wKB67fnjsFS1D0PgnoIQyepLgvMpoNQSaJy
zZ077TVlgJLpoHXaKtvrH1HIAUr6lmU3Smu3Lpcg5pTWLkSkhTmcDYCUxJrBmJZT
yfz6MiVheI1j34lPyKh7wr8cmalyUkjBU9dmmUs0bf95HeiRhEE/FyHaaQApzvqP
QzCNOkc1DovtfWZXEth6cpPenCw9NhN+7vBtFGjo5LZF2H5Dxiq2Ke41AgMBAAGj
ggI3MIICMzAOBgNVHQ8BAf8EBAMCBaAwHQYDVR0OBBYEFNOhbF3QVIoW9y7eVlTF
WatADC6mMB8GA1UdIwQYMBaAFFE2ZtWOxAs/5DyGRkkfRdZ55HJQMIHaBgNVHR8E
gdIwgc8wgcyggcmggcaGgcNsZGFwOi8vL0NOPXRlc3RjaXNjby1SVFdPUkstUEMx
LUNBLENOPXJ0d29yay1wYzEsQ049Q0RQLENOPVB1YmxpYyUyMEtleSUyMFNlcnZp
Y2VzLENOPVNlcnZpY2VzLENOPUNvbmZpZ3VyYXRpb24sREM9dGVzdGNpc2NvLERD
PWNvbT9jZXJ0aWZpY2F0ZVJldm9jYXRpb25MaXN0P2Jhc2U/b2JqZWN0Q2xhc3M9
Y1JMRGlzdHJpYnV0aW9uUG9pbnQwgcsGCCsGAQUFBwEBBIG+MIG7MIG4BggrBgEF
BQcwAoaBq2xkYXA6Ly8vQ049dGVzdGNpc2NvLVJUV09SSy1QQzEtQ0EsQ049QUlB
LENOPVB1YmxpYyUyMEtleSUyMFNlcnZpY2VzLENOPVNlcnZpY2VzLENOPUNvbmZp
Z3VyYXRpb24sREM9dGVzdGNpc2NvLERDPWNvbT9jQUNlcnRpZmljYXRlP2Jhc2U/
b2JqZWN0Q2xhc3M9Y2VydGlmaWNhdGlvbkF1dGhvcml0eTAhBgkrBgEEAYI3FAIE
FB4SAFcAZQBiAFMAZQByAHYAZQByMBMGA1UdJQQMMAoGCCsGAQUFBwMBMA0GCSqG
SIb3DQEBBQUAA4IBAQCLKYPzDso/j9e1C5p6bGxuTvtOLqFUiuG+De3r/SYXSxA5
Y2PiOhzzjrUU35ccMLRXwGCZ5J8u7ycMZVBAG49QhLhIRp7F9Dpn20YM7zKKwfKW
gpVYjLSIJnlpyG69xcgwGBg85T7l6YOTwzRg3+SO9lGeD5PftelKB1/qTmwo+uv9
XvnOpIeCliiqgRGwc6yW7JOVA36JS6jNb9ThtXTdmnz4JlSqm8XU9kY79r0NCzkG
YtlU7AwjRFFTjSifrJvCG/sMkPe85JQFiB2Ikwk+ayoLOwMLM37EYF+vqkGx499f
YCmxWTdSwgvNQkTVQ7toiyn6WAb29MUZvzQcc0Du
-----END CERTIFICATE-----
-----END CERTIFICATE-----
quit
% Router Certificate successfully imported
Spoke-01#show crypto pki certificates # 查看证书
Certificate
Status: Available
Certificate Serial Number (hex): 310000000AB9A3BD15FD1EB75900000000000A
Certificate Usage: General Purpose
Issuer:
cn=testcisco-RTWORK-PC1-CA
dc=testcisco
dc=com
Subject:
Name: spoke01
cn=spoke01
dc=testcisco
dc=com
CRL Distribution Points:
ldap:///CN=testcisco-RTWORK-PC1-CA,CN=rtwork-pc1,CN=CDP,CN=Public%20Key%20Services,CN=Services,CN=Configuration,DC=testcisco,DC=com?certificateRevocationList?base?objectClass=cRLDistributionPoint
Validity Date:
start date: 15:43:48 CST Jan 25 2021
end date: 15:43:48 CST Jan 25 2023
Associated Trustpoints: testca
CA Certificate
Status: Available
Certificate Serial Number (hex): 6EBF1DA0EB361BBE4B71CB7EC6BE692D
Certificate Usage: Signature
Issuer:
cn=testcisco-RTWORK-PC1-CA
dc=testcisco
dc=com
Subject:
cn=testcisco-RTWORK-PC1-CA
dc=testcisco
dc=com
Validity Date:
start date: 11:00:35 CST Jan 25 2021
end date: 04:42:18 CST Dec 20 1944
Associated Trustpoints: testca
- DMVPN环境配置
crypto isakmp enable
crypto isakmp policy 10
encr aes
hash sha256
authentication rsa-sig
lifetime 86400
group 2
crypto isakmp invalid-spi-recovery
crypto isakmp keepalive 30 10 periodic
crypto isakmp nat keepalive 360
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association replay disable
crypto ipsec transform-set 3DES esp-3des esp-sha-hmac
mode transport
crypto ipsec nat-transparency spi-matching
crypto ipsec profile NEPROF-MKT
set transform-set 3DES
set pfs group2
interface Tunnel20
description DMVPN-HUB
bandwidth 1000000
ip address 10.16.1.1 255.255.255.0
no ip redirects
ip mtu 1400
ip nhrp map 10.16.1.10 123.1.1.10
ip nhrp map multicast 123.1.1.10
ip nhrp nhs 10.16.1.10
ip nhrp authentication cisco
ip nhrp map multicast dynamic
ip nhrp network-id 20
ip nhrp holdtime 300
ip tcp adjust-mss 1360
ip ospf network broadcast
ip ospf priority 95
ip ospf cost 2000
load-interval 30
delay 1000
tunnel source Ethernet0/0
tunnel mode gre multipoint
tunnel key 20
tunnel path-mtu-discovery
tunnel bandwidth transmit 100000
tunnel bandwidth receive 100000
tunnel protection ipsec profile NEPROF-MKT
- OSPF路由环境配置
interface Loopback0
ip address 192.168.1.1 255.255.255.0
ip ospf network point-to-point
ip ospf 100 area 1
router ospf 100
network 10.16.1.0 0.0.0.255 area 0
Spoke-02
证书的申请和导入详细部分请参考HUB配置,这里只做简单阐述和标记变动的地方。
- 导入CA证书并信任
Spoke-02(config)#crypto key generate rsa modulus 2048 label spoke02-key # 需要先产生密钥对
Spoke-02(config)#crypto pki trustpoint testca # 定义CA证书名称
Spoke-02(ca-trustpoint)#enrollment terminal # 定义证书获得方式,手动导入
Spoke-02(ca-trustpoint)#subject-name cn=spoke02,dc=testcisco,dc=com
Spoke-02(ca-trustpoint)#revocation-check none # 不检查证书是否吊销
Spoke-02(ca-trustpoint)#rsakeypair spoke02-key # 调用密钥对
# 使用命令crypto pki authenticate testca,导入testca的根证书
Spoke-02(config)#crypto pki authenticate testca
Enter the base 64 encoded CA certificate.
End with a blank line or the word "quit" on a line by itself
-----BEGIN CERTIFICATE-----
MIIDgTCCAmmgAwIBAgIQbr8doOs2G75Lcct+xr5pLTANBgkqhkiG9w0BAQUFADBS
MRMwEQYKCZImiZPyLGQBGRYDY29tMRkwFwYKCZImiZPyLGQBGRYJdGVzdGNpc2Nv
MSAwHgYDVQQDExd0ZXN0Y2lzY28tUlRXT1JLLVBDMS1DQTAgFw0yMTAxMjUwMzAw
MzVaGA8yMDgxMDEyNTAzMTAzNFowUjETMBEGCgmSJomT8ixkARkWA2NvbTEZMBcG
CgmSJomT8ixkARkWCXRlc3RjaXNjbzEgMB4GA1UEAxMXdGVzdGNpc2NvLVJUV09S
Sy1QQzEtQ0EwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDW5ukULFmn
X53mWUmyAOyYl5yF7yzux25GgBPqCW5qYZSWDBARY0oVuCOvnv1sGJOG0GUnrC31
Sqhn3uHvucxtKhDYD2g2LMQH76kO1xR7QYmylm/VdC9+uLbV+9c8atCaJddHw5lf
ghLdRfoTQMmwVxA3gJIFxKALNPvSFF+Zg1fo9Iuq1FE3zsHSuox2YIQRoz9YUyyy
rTpZW7JBMdu0/OCRhgTu1KqdhYdlB/QspSEW5Cs5b/mXbHsOCy6aeqS7HuBaV4Vb
mX3lcE+1icyeMK9BzhM+jcpW+DlP0F0py0LuNz71ZiQ1zOj3UkOORb9+XzyMr0u6
co64pVFF9y+pAgMBAAGjUTBPMAsGA1UdDwQEAwIBhjAPBgNVHRMBAf8EBTADAQH/
MB0GA1UdDgQWBBRRNmbVjsQLP+Q8hkZJH0XWeeRyUDAQBgkrBgEEAYI3FQEEAwIB
ADANBgkqhkiG9w0BAQUFAAOCAQEAQI4KQRQZ49K2LLdiy51D9tmrIRbidZXLdpRE
eylKlXwrOJoJrdcSKgbLD94ycUIgiqlsNtIzDal0l5IKprILfI3vB7dK4e4iZ1G8
GGEERJJKtpZ/uJ3eGzLSbOsfQ1c6z5d2+8ske0AR31WPSpO5c6HQauur0QRdtKYw
iLEMF3/AGPKIM5j5EOwKpP4mG48wIg4dStI4vjGFHwlpaZfVYjj9qX/1SJVLswSK
4WqpXTZFVMOaplPAyGY7c+St8wULGOwql3hPb1IZNYBB0nQGRFeo7y42czyw8dUz
k4VH7IrGEoIWh5u1r66WBMsLTDG+UbqF96BJxHgyp5VPp3Xo8A==
-----END CERTIFICATE-----
quit
# 并用quit命令退出根证书,退出后系统会弹出对话框,询问是否接受证书
Certificate has the following attributes:
Fingerprint MD5: 25A595E5 3F591617 B82E80E1 16686B51
Fingerprint SHA1: 1F28E4B2 BF190E40 453169E4 21D1C4AD 45897B54
% Do you accept this certificate? [yes/no]: yes # 输入yes接受证书。
Trustpoint CA certificate accepted.
% Certificate successfully imported
- 申请路由器证书并导入
Spoke-02(config)#crypto pki enroll testca # 创建证书请求
% Start certificate enrollment ..
% The subject name in the certificate will include: cn=spoke02,dc=testcisco,dc=com
% The subject name in the certificate will include: Spoke-02.cisco.com
% Include the router serial number in the subject name? [yes/no]: no
% Include an IP address in the subject name? [no]: no
Display Certificate Request to terminal? [yes/no]: yes
Certificate Request follows:
MIICyzCCAbMCAQAwZTETMBEGCgmSJomT8ixkARkWA2NvbTEZMBcGCgmSJomT8ixk
ARkWCXRlc3RjaXNjbzEQMA4GA1UEAxMHc3Bva2UwMjEhMB8GCSqGSIb3DQEJAhYS
U3Bva2UtMDIuY2lzY28uY29tMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKC
AQEA4FgbXAdYF1Rlqu60+JaU9/YXL1QOTmNiggoC26O8F2PMwXvYuOrOs8MjdiJS
j4tVrzMkZ/VXwThDO8xoxyMLSa5bj0qkyw6QtUFPiROGBi8RUAKQ08IXwkytwMVs
Pi1yIccH0AvodJh+ckfkCBgZSSVEcMUC9CE4VJ+d3WdrFu3qNNg83CCSVCBtMldI
ldFt/aCJ4nKBm/QaNOHxSDPjuwW5sKDpNt2G4PkemJdDqGRpOX6l7UIqQZj/W/eJ
yvUflFKPxRkzbSBSh5h/da5k2V3YHhBybd6Row465nO+RtUYJ+EgXorVSKJvb5BO
5QreDE6iQrtzJF1hxbK02iEicQIDAQABoCEwHwYJKoZIhvcNAQkOMRIwEDAOBgNV
HQ8BAf8EBAMCBaAwDQYJKoZIhvcNAQEFBQADggEBAJW8QtQzmvwqvhBMbSxmM0Ev
tmakLG5adPIFuHT/lPLRUHjgJ2ZL9ZdcqOnzVniazuFal5FHSaSMlMeH8K9Zx+3r
0YzyAmtYRY0iTDjcaRVp/MbUkkHhzuT+mnumhTEO9pyvn+FmzqzK1BUD8B6Ln9LE
KtQ/lE56Z+kPxnDvQJmM/fgVCVediSb6DyJxl7y7rQ+bA0deh5hvM3PNov9DmhTr
tnidYz1KUn22G55Epf9XfouhQ8VrIanPfQkXcXAQupR7w/2Bfr3nCb2qXXugMois
uRi0eXE98Yeg2qyp+92oAgq7PBzoVfY6wzejvtQCmYAFHbU8Pbx7bs2MovfNIVI=
---End - This line not part of the certificate request---
Redisplay enrollment request? [yes/no]: no
Spoke-02(config)#crypto pki import testca certificate # 导入证书
Enter the base 64 encoded certificate.
End with a blank line or the word "quit" on a line by itself
-----BEGIN CERTIFICATE-----
MIIFWjCCBEKgAwIBAgITMQAAAAvOaZeioWndPQAAAAAACzANBgkqhkiG9w0BAQUF
ADBSMRMwEQYKCZImiZPyLGQBGRYDY29tMRkwFwYKCZImiZPyLGQBGRYJdGVzdGNp
c2NvMSAwHgYDVQQDExd0ZXN0Y2lzY28tUlRXT1JLLVBDMS1DQTAeFw0yMTAxMjUw
ODAwMDlaFw0yMzAxMjUwODAwMDlaMEIxEzARBgoJkiaJk/IsZAEZFgNjb20xGTAX
BgoJkiaJk/IsZAEZFgl0ZXN0Y2lzY28xEDAOBgNVBAMTB3Nwb2tlMDIwggEiMA0G
CSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDgWBtcB1gXVGWq7rT4lpT39hcvVA5O
Y2KCCgLbo7wXY8zBe9i46s6zwyN2IlKPi1WvMyRn9VfBOEM7zGjHIwtJrluPSqTL
DpC1QU+JE4YGLxFQApDTwhfCTK3AxWw+LXIhxwfQC+h0mH5yR+QIGBlJJURwxQL0
IThUn53dZ2sW7eo02DzcIJJUIG0yV0iV0W39oInicoGb9Bo04fFIM+O7BbmwoOk2
3Ybg+R6Yl0OoZGk5fqXtQipBmP9b94nK9R+UUo/FGTNtIFKHmH91rmTZXdgeEHJt
3pGjDjrmc75G1Rgn4SBeitVIom9vkE7lCt4MTqJCu3MkXWHFsrTaISJxAgMBAAGj
ggI3MIICMzAOBgNVHQ8BAf8EBAMCBaAwHQYDVR0OBBYEFEPJotqjmNVumF3qdqlN
UsbknC7oMB8GA1UdIwQYMBaAFFE2ZtWOxAs/5DyGRkkfRdZ55HJQMIHaBgNVHR8E
gdIwgc8wgcyggcmggcaGgcNsZGFwOi8vL0NOPXRlc3RjaXNjby1SVFdPUkstUEMx
LUNBLENOPXJ0d29yay1wYzEsQ049Q0RQLENOPVB1YmxpYyUyMEtleSUyMFNlcnZp
Y2VzLENOPVNlcnZpY2VzLENOPUNvbmZpZ3VyYXRpb24sREM9dGVzdGNpc2NvLERD
PWNvbT9jZXJ0aWZpY2F0ZVJldm9jYXRpb25MaXN0P2Jhc2U/b2JqZWN0Q2xhc3M9
Y1JMRGlzdHJpYnV0aW9uUG9pbnQwgcsGCCsGAQUFBwEBBIG+MIG7MIG4BggrBgEF
BQcwAoaBq2xkYXA6Ly8vQ049dGVzdGNpc2NvLVJUV09SSy1QQzEtQ0EsQ049QUlB
LENOPVB1YmxpYyUyMEtleSUyMFNlcnZpY2VzLENOPVNlcnZpY2VzLENOPUNvbmZp
Z3VyYXRpb24sREM9dGVzdGNpc2NvLERDPWNvbT9jQUNlcnRpZmljYXRlP2Jhc2U/
b2JqZWN0Q2xhc3M9Y2VydGlmaWNhdGlvbkF1dGhvcml0eTAhBgkrBgEEAYI3FAIE
FB4SAFcAZQBiAFMAZQByAHYAZQByMBMGA1UdJQQMMAoGCCsGAQUFBwMBMA0GCSqG
SIb3DQEBBQUAA4IBAQBARLj2AvCH1VAHFOsoKPyEQeesQwLaLjB6G08fxEAF7jWb
lYOCfF08++qwr9Vtgos5pLf58wXO4+VfHxP+pDRtSK2ar9Y7K1Czvd0blActJfH3
udNoZl71tw7ITX7kR+p5zAJMlvbmTtPaoV0EWcoIvfHxv1utqimWtiqunA0q+lVV
dIM0KYyqO54ZgcPcMfpJs8dc0fk00YLz9bmkzPTrjsYTW5bGIdSU9LsAzeAmtZq1
gSTnR85FuPi6G8CzcDovy6VupJSv4Eaq35a0FG77ykqD/CgzdlxGtDYe5Q5z+BY1
kDtLcsV/KVjDT1vgH4/u0Ec6+uspHTHfrGDP6uoQ
-----END CERTIFICATE-----
quit
% Router Certificate successfully imported
Spoke-02#show crypto pki certificates # 查看证书
Certificate
Status: Available
Certificate Serial Number (hex): 310000000BCE6997A2A169DD3D00000000000B
Certificate Usage: General Purpose
Issuer:
cn=testcisco-RTWORK-PC1-CA
dc=testcisco
dc=com
Subject:
Name: spoke02
cn=spoke02
dc=testcisco
dc=com
CRL Distribution Points:
ldap:///CN=testcisco-RTWORK-PC1-CA,CN=rtwork-pc1,CN=CDP,CN=Public%20Key%20Services,CN=Services,CN=Configuration,DC=testcisco,DC=com?certificateRevocationList?base?objectClass=cRLDistributionPoint
Validity Date:
start date: 16:00:09 CST Jan 25 2021
end date: 16:00:09 CST Jan 25 2023
Associated Trustpoints: testca
CA Certificate
--More--
Jan 25 16:12:47 CST: %SYS-5-CONFIG_I: Configured from console by console
Status: Available
Certificate Serial Number (hex): 6EBF1DA0EB361BBE4B71CB7EC6BE692D
Certificate Usage: Signature
Issuer:
cn=testcisco-RTWORK-PC1-CA
dc=testcisco
dc=com
Subject:
cn=testcisco-RTWORK-PC1-CA
dc=testcisco
dc=com
Validity Date:
start date: 11:00:35 CST Jan 25 2021
end date: 04:42:18 CST Dec 20 1944
Associated Trustpoints: testca
- DMVPN环境配置
crypto isakmp enable
crypto isakmp policy 10
encr aes
hash sha256
authentication rsa-sig
lifetime 86400
group 2
crypto isakmp invalid-spi-recovery
crypto isakmp keepalive 30 10 periodic
crypto isakmp nat keepalive 360
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association replay disable
crypto ipsec transform-set 3DES esp-3des esp-sha-hmac
mode transport
crypto ipsec nat-transparency spi-matching
crypto ipsec profile NEPROF-MKT
set transform-set 3DES
set pfs group2
interface Tunnel20
description DMVPN-HUB
bandwidth 1000000
ip address 10.16.1.2 255.255.255.0
no ip redirects
ip mtu 1400
ip nhrp map 10.16.1.10 123.1.1.10
ip nhrp map multicast 123.1.1.10
ip nhrp nhs 10.16.1.10
ip nhrp authentication cisco
ip nhrp map multicast dynamic
ip nhrp network-id 20
ip nhrp holdtime 300
ip tcp adjust-mss 1360
ip ospf network broadcast
ip ospf priority 95
ip ospf cost 2000
load-interval 30
delay 1000
tunnel source Ethernet0/0
tunnel mode gre multipoint
tunnel key 20
tunnel path-mtu-discovery
tunnel bandwidth transmit 100000
tunnel bandwidth receive 100000
tunnel protection ipsec profile NEPROF-MKT
- OSPF路由环境配置
interface Loopback0
ip address 192.168.2.1 255.255.255.0
ip ospf network point-to-point
ip ospf 100 area 2
router ospf 100
network 10.16.1.0 0.0.0.255 area 0
DMVPN路由器为CA和证书服务器
需要参考上文中基础配置部分,该部分为通用配置本章节将不会再次说明。
HUB-CA 配置IOS路由器为CA
- 配置HUB路由器为CA
- 激活HTTP服务
Hub-CA(config)#ip http server
- 创建并激活CA服务
crypto pki server ca:开启证书服务器,ca是证书服务器名称
issuer-name O=tech CN=cisco C=com:配置颁布者信息(后面都是自定义的),O表示组织,CN表示证书名,C表示国家
database url nvram:指定证书存放在哪里
database level minimum:当用户申请证书时,配置用户的证书存储类型,有三个类型:
minimum:默认配置,仅仅存储证书的基本信息
names:除了证书的基本信息,还同时保存每一个证书的序列号和证书标题等附加信息
complete:包含前两项信息,还会将证书写入到数据库,需要较大空间,通常使用TFTP存储
lifetime ca-certificate 7305:设置CA证书的过期时间(单位为天)
lifetime certificate 720:客户端申请的证书过期时间(单位为天)
grant auto:当客户端申请证书时,自动颁发证书给客户端
no shutdown:激活CA服务器,并设置当客户端申请证书时需要输入的密码
Hub-CA(config)#crypto pki server ca
Hub-CA(cs-server)#issuer-name O=tech CN=cisco C=com
Hub-CA(cs-server)#database url nvram:
Hub-CA(cs-server)#database level minimum
Hub-CA(cs-server)#lifetime ca-certificate 3600
Hub-CA(cs-server)#lifetime certificate 720
Hub-CA(cs-server)#no shutdown
%Some server settings cannot be changed after CA certificate generation.
% Please enter a passphrase to protect the private key
% or type Return to exit
Password:1a.Cisco
Re-enter password:1a.Cisco
% Generating 1024 bit RSA keys, keys will be non-exportable...
[OK] (elapsed time was 0 seconds)
Hub-CA#show crypto pki server # 查看服务器状态
Certificate Server ca:
Status: enabled
State: enabled
Server's configuration is locked (enter "shut" to unlock it)
Issuer name: O=tech CN=cisco C=com
CA cert fingerprint: FC4D60C6 E3E917BD 402AF09E 8B759D28
Granting mode is: manual
Last certificate issued serial number (hex): 1
CA certificate expiration timer: 16:26:54 GMT Dec 4 2030
CRL NextUpdate timer: 22:26:54 GMT Jan 25 2021
Current primary storage dir: nvram:
Database Level: Minimum - no cert data written to storage
- 客户端申请证书
- 产生密钥
rsa:是数据加密算法label dmvpn-hub:给这个key起个字modulus 1024:设定key的长度,默认是512exportable表示可以把key导出来storage nvram:结合exportable,导出到nvram,也可以导出到tftp或flash
Hub-CA(config)#crypto key generate rsa general-keys label dmvpn-hub exportable storage nvram modulus 2048
The name for the keys will be: dmvpn-hub
% The key modulus size is 2048 bits
% Generating 2048 bit RSA keys, keys will be exportable...
[OK] (elapsed time was 1 seconds)
- 验证CA证书
crypto pki trustpoint dmvpn-cert:指定信任点(即证书服务器),abc是信任点名称
enrollment url http://123.1.1.10:到哪里去拿证书,这里是与证书服务器相连的接口
subject-name O=tech CN=Hub CN=cisco C=com:配置证书使用者的信息
crypto pki authenticate dmvpn-cert:从信任点(即证书服务器)请求并下载CA根证书
Hub-CA(config)#crypto pki trustpoint dmvpn-cert
Hub-CA(ca-trustpoint)#enrollment url http://123.1.1.10
Hub-CA(ca-trustpoint)#subject-name O=tech CN=Hub CN=cisco C=com
Hub-CA(ca-trustpoint)#rsakeypair dmvpn-hub
Hub-CA(ca-trustpoint)#exit
Hub-CA(config)#crypto pki authenticate dmvpn-cert
Certificate has the following attributes:
Fingerprint MD5: 73C758FF 008D3D00 29541BBC DAD2E85A
Fingerprint SHA1: 0BCD7F3C 023B031F 46B1FF42 64A7121B EB797945
% Do you accept this certificate? [yes/no]: yes
Trustpoint CA certificate accepted.
- 在线申请证书
Hub-CA(config)#crypto pki enroll dmvpn-cert
%
% Start certificate enrollment ..
% Create a challenge password. You will need to verbally provide this
password to the CA Administrator in order to revoke your certificate.
For security reasons your password will not be saved in the configuration.
Please make a note of it.
Password:
Re-enter password:
% The subject name in the certificate will include: O=tech CN=Hub CN=cisco C=com
% The subject name in the certificate will include: Hub-CA.cisco.com
% Include the router serial number in the subject name? [yes/no]: yes
% The serial number in the certificate will be: 67108880
% Include an IP address in the subject name? [no]: no
Request certificate from CA? [yes/no]: yes
% Certificate request sent to Certificate Authority
% The 'show crypto pki certificate verbose dmvpn-cert' commandwill show the fingerprint.
Jan 25 16:58:56 GMT: CRYPTO_PKI: Certificate Request Fingerprint MD5: 00FF6481 BF286467 14C80C36 F6FC012A
Jan 25 16:58:56 GMT: CRYPTO_PKI: Certificate Request Fingerprint SHA1: 961D4D29 613F9ED7 9A459CE5 B5D44148 A65884B8
- CA审核、签名、颁发证书
- CA查看证书请求
Hub-CA#show crypto pki server ca requests
Enrollment Request Database:
Subordinate CA certificate requests:
ReqID State Fingerprint SubjectName
--------------------------------------------------------------
RA certificate requests:
ReqID State Fingerprint SubjectName
--------------------------------------------------------------
Router certificates requests:
ReqID State Fingerprint SubjectName
--------------------------------------------------------------
1 pending 00FF6481BF28646714C80C36F6FC012A serialNumber=67108880+hostname=Hub-CA.cisco.com,o=tech CN=Hub CN=cisco C=com
- CA签发证书
Hub-CA#crypto pki server ca grant 1
# 客户端收到签发消息
Jan 25 17:02:56 GMT: %PKI-6-CERTRET: Certificate received from Certificate Authority
Hub-CA#show crypto pki certificates # 查看证书已是可用状态
Certificate
Status: Available
Certificate Serial Number (hex): 02
Certificate Usage: General Purpose
Issuer:
o=tech CN=cisco C=com
Subject:
Name: Hub-CA.cisco.com
Serial Number: 67108880
serialNumber=67108880+hostname=Hub-CA.cisco.com
o=tech CN=Hub CN=cisco C=com
Validity Date:
start date: 17:02:53 GMT Jan 25 2021
end date: 17:02:53 GMT Jan 15 2023
Associated Trustpoints: dmvpn-cert
CA Certificate
Status: Available
Certificate Serial Number (hex): 01
Certificate Usage: Signature
Issuer:
o=tech CN=cisco C=com
Subject:
o=tech CN=cisco C=com
Validity Date:
start date: 16:52:43 GMT Jan 25 2021
end date: 16:52:43 GMT Dec 4 2030
Associated Trustpoints: dmvpn-cert ca
- 配置DMVPN环境
crypto isakmp enable
crypto isakmp policy 10
encr aes
hash sha256
authentication rsa-sig
lifetime 86400
group 2
crypto isakmp invalid-spi-recovery
crypto isakmp keepalive 30 10 periodic
crypto isakmp nat keepalive 360
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association replay disable
crypto ipsec transform-set 3DES esp-3des esp-sha-hmac
mode transport
crypto ipsec nat-transparency spi-matching
crypto ipsec profile NEPROF-MKT
set transform-set 3DES
set pfs group2
interface Tunnel20
description DMVPN-HUB
bandwidth 1000000
ip address 10.16.1.10 255.255.255.0
no ip redirects
ip mtu 1400
ip nhrp authentication cisco
ip nhrp map multicast dynamic
ip nhrp network-id 20
ip nhrp holdtime 300
ip tcp adjust-mss 1360
ip ospf network broadcast
ip ospf priority 95
ip ospf cost 2000
load-interval 30
delay 1000
tunnel source Ethernet0/0
tunnel mode gre multipoint
tunnel key 20
tunnel path-mtu-discovery
tunnel bandwidth transmit 100000
tunnel bandwidth receive 100000
tunnel protection ipsec profile NEPROF-MKT
- 配置OSPF环境
interface Loopback0
ip address 192.168.10.1 255.255.255.0
ip ospf network point-to-point
ip ospf 100 area 10
router ospf 100
network 10.16.1.0 0.0.0.255 area 0
Spoke-01(在线方式)
- 申请证书
Spoke-01(config)#crypto key generate rsa general-keys label Spoke-01 exportable storage nvram modulus 2048
Spoke-01(config)#crypto pki trustpoint dmvpn-cert
Spoke-01(ca-trustpoint)#enrollment url http://123.1.1.10
Spoke-01(ca-trustpoint)#rsakeypair Spoke-01
Spoke-01(ca-trustpoint)#subject-name O=tech CN=Spoke-01 CN=cisco C=com
Spoke-01(ca-trustpoint)#exit
Spoke-01(config)#crypto pki authenticate dmvpn-cert
Certificate has the following attributes:
Fingerprint MD5: 73C758FF 008D3D00 29541BBC DAD2E85A
Fingerprint SHA1: 0BCD7F3C 023B031F 46B1FF42 64A7121B EB797945
% Do you accept this certificate? [yes/no]: yes
Trustpoint CA certificate accepted.
Spoke-01(config)#crypto pki enroll dmvpn-cert
%
% Start certificate enrollment ..
% Create a challenge password. You will need to verbally provide this
password to the CA Administrator in order to revoke your certificate.
For security reasons your password will not be saved in the configuration.
Please make a note of it.
Password:
Re-enter password:
% The subject name in the certificate will include: O=tech CN=Spoke-01 CN=cisco C=com
% The subject name in the certificate will include: Spoke-01.cisco.com
% Include the router serial number in the subject name? [yes/no]: no
% Include an IP address in the subject name? [no]: no
Request certificate from CA? [yes/no]: yes
% Certificate request sent to Certificate Authority
% The 'show crypto pki certificate verbose dmvpn-cert' commandwill show the fingerprint.
Jan 25 13:46:42 CST: CRYPTO_PKI: Certificate Request Fingerprint MD5: 7B751FDB 7C01B337 8C5D5821 346B8BA3
Jan 25 13:46:42 CST: CRYPTO_PKI: Certificate Request Fingerprint SHA1: 6A4B258B AD9D86FB 3AA78476 1C9892AC CAEAD0C0
Jan 25 13:46:42 CST: %PKI-6-CERTRET: Certificate received from Certificate Authority
Spoke-01#show crypto pki certificates # 待CA签发证书以后,查看收到的证书。
Certificate
Status: Available
Certificate Serial Number (hex): 03
Certificate Usage: General Purpose
Issuer:
o=tech CN=cisco C=com
Subject:
Name: Spoke-01.cisco.com
hostname=Spoke-01.cisco.com
o=tech CN=Spoke-01 CN=cisco C=com
Validity Date:
start date: 17:07:19 CST Jan 25 2021
end date: 17:07:19 CST Jan 15 2023
Associated Trustpoints: dmvpn-cert
CA Certificate
Status: Available
Certificate Serial Number (hex): 01
Certificate Usage: Signature
Issuer:
o=tech CN=cisco C=com
Subject:
o=tech CN=cisco C=com
Validity Date:
start date: 16:52:43 CST Jan 25 2021
end date: 16:52:43 CST Dec 4 2030
Associated Trustpoints: dmvpn-cert
- 配置DMVPN环境
crypto isakmp enable
crypto isakmp policy 10
encr aes
hash sha256
authentication rsa-sig
lifetime 86400
group 2
crypto isakmp invalid-spi-recovery
crypto isakmp keepalive 30 10 periodic
crypto isakmp nat keepalive 360
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association replay disable
crypto ipsec transform-set 3DES esp-3des esp-sha-hmac
mode transport
crypto ipsec nat-transparency spi-matching
crypto ipsec profile NEPROF-MKT
set transform-set 3DES
set pfs group2
interface Tunnel20
description DMVPN-HUB
bandwidth 1000000
ip address 10.16.1.1 255.255.255.0
no ip redirects
ip mtu 1400
ip nhrp map 10.16.1.10 123.1.1.10
ip nhrp map multicast 123.1.1.10
ip nhrp nhs 10.16.1.10
ip nhrp authentication cisco
ip nhrp map multicast dynamic
ip nhrp network-id 20
ip nhrp holdtime 300
ip tcp adjust-mss 1360
ip ospf network broadcast
ip ospf priority 95
ip ospf cost 2000
load-interval 30
delay 1000
tunnel source Ethernet0/0
tunnel mode gre multipoint
tunnel key 20
tunnel path-mtu-discovery
tunnel bandwidth transmit 100000
tunnel bandwidth receive 100000
tunnel protection ipsec profile NEPROF-MKT
- 配置OSPF网络环境
interface Loopback0
ip address 192.168.1.1 255.255.255.0
ip ospf network point-to-point
ip ospf 100 area 1
router ospf 100
network 10.16.1.0 0.0.0.255 area 0
Spoke-02(离线方式)
- 产生密钥对,并验证CA。
Spoke-02(config)#crypto key generate rsa general-keys label Spoke-02 exportable storage nvram modulus 2048
Spoke-02(config)#crypto pki trustpoint dmvpn-cert
Spoke-02(ca-trustpoint)#enrollment terminal
Spoke-02(ca-trustpoint)#rsakeypair Spoke-02
Spoke-02(ca-trustpoint)#subject-name O=tech CN=Spoke-02 CN=cisco C=com
Spoke-02(ca-trustpoint)#revocation-check none
Spoke-02(ca-trustpoint)#exit
- CA导出证书
Hub-CA(config)#crypto pki export ca pem terminal
% The specified trustpoint is not enrolled (ca).
% Only export the CA certificate in PEM format.
% CA certificate:
-----BEGIN CERTIFICATE-----
MIICFTCCAX6gAwIBAgIBATANBgkqhkiG9w0BAQQFADAeMRwwGgYDVQQKExN0ZWNo
IENOPWNpc2NvIEM9Y29tMB4XDTIxMDEyNTA4NTI0M1oXDTMwMTIwNDA4NTI0M1ow
HjEcMBoGA1UEChMTdGVjaCBDTj1jaXNjbyBDPWNvbTCBnzANBgkqhkiG9w0BAQEF
AAOBjQAwgYkCgYEAnuLd1gUI4913i4ywz2IUEhZ7vovIa/rDaKrWk1QpXSD5hk18
oOM6g9A1UDjwY8zdz8G+/vB9VzBtf4C6rkVQHJSlDt8hA8fqOjuQnN10qN1oD5eP
H/+PbYwq1zm6wv3vve+iUnqYLQBQR8uCJAxhy/tHePo/ldRJkeh4aURdE28CAwEA
AaNjMGEwDwYDVR0TAQH/BAUwAwEB/zAOBgNVHQ8BAf8EBAMCAYYwHwYDVR0jBBgw
FoAUIeeFkyaiIRjw7j1oySP2EgU7ALcwHQYDVR0OBBYEFCHnhZMmoiEY8O49aMkj
9hIFOwC3MA0GCSqGSIb3DQEBBAUAA4GBAIupXvYzDXtHssGHrPUvhyS5xps+vfhJ
Ftnkg3RjtrHKsuj7rg09/cIT7PT8+mr/5o0dj98G7TN6+JCfSHKNZ11MwIiNNuEs
FcWfQTaSVACYXCG7U3wYW8aS1xIpg0lhocM3tE4EfqHYsWfwMBytw3td0eYsKAkY
1XLcIHV4w/ah
-----END CERTIFICATE-----
- Spoke-02导入CA证书
Spoke-02(config)#crypto pki authenticate dmvpn-cert
Enter the base 64 encoded CA certificate.
End with a blank line or the word "quit" on a line by itself
-----BEGIN CERTIFICATE-----
MIICFTCCAX6gAwIBAgIBATANBgkqhkiG9w0BAQQFADAeMRwwGgYDVQQKExN0ZWNo
IENOPWNpc2NvIEM9Y29tMB4XDTIxMDEyNTA4NTI0M1oXDTMwMTIwNDA4NTI0M1ow
HjEcMBoGA1UEChMTdGVjaCBDTj1jaXNjbyBDPWNvbTCBnzANBgkqhkiG9w0BAQEF
AAOBjQAwgYkCgYEAnuLd1gUI4913i4ywz2IUEhZ7vovIa/rDaKrWk1QpXSD5hk18
oOM6g9A1UDjwY8zdz8G+/vB9VzBtf4C6rkVQHJSlDt8hA8fqOjuQnN10qN1oD5eP
H/+PbYwq1zm6wv3vve+iUnqYLQBQR8uCJAxhy/tHePo/ldRJkeh4aURdE28CAwEA
AaNjMGEwDwYDVR0TAQH/BAUwAwEB/zAOBgNVHQ8BAf8EBAMCAYYwHwYDVR0jBBgw
FoAUIeeFkyaiIRjw7j1oySP2EgU7ALcwHQYDVR0OBBYEFCHnhZMmoiEY8O49aMkj
9hIFOwC3MA0GCSqGSIb3DQEBBAUAA4GBAIupXvYzDXtHssGHrPUvhyS5xps+vfhJ
Ftnkg3RjtrHKsuj7rg09/cIT7PT8+mr/5o0dj98G7TN6+JCfSHKNZ11MwIiNNuEs
FcWfQTaSVACYXCG7U3wYW8aS1xIpg0lhocM3tE4EfqHYsWfwMBytw3td0eYsKAkY
1XLcIHV4w/ah
-----END CERTIFICATE-----
quit
Certificate has the following attributes:
Fingerprint MD5: 42375DEC 0F1E8449 7C14D441 50D453D3
Fingerprint SHA1: 6ED7D563 78E906F1 1D20A005 9BE3D7E3 558EE21A
% Do you accept this certificate? [yes/no]: yes
Trustpoint CA certificate accepted.
% Certificate successfully imported
Spoke-02#show crypto pki certificates # 查看CA证书
CA Certificate
Status: Available
Certificate Serial Number (hex): 01
Certificate Usage: Signature
Issuer:
o=tech CN=cisco C=com
Subject:
o=tech CN=cisco C=com
Validity Date:
start date: 16:52:43 CST Jan 25 2021
end date: 16:52:43 CST Dec 4 2030
Associated Trustpoints: dmvpn-cert
- 申请证书,并导入。
- 产生证书申请请求
Spoke-02(config)#crypto pki enroll dmvpn-cert
% Start certificate enrollment ..
% The subject name in the certificate will include: O=tech CN=Spoke-02 CN=cisco C=com
% The subject name in the certificate will include: Spoke-02.cisco.com
% Include the router serial number in the subject name? [yes/no]: no
% Include an IP address in the subject name? [no]: no
Display Certificate Request to terminal? [yes/no]: yes
Certificate Request follows:
MIICszCCAZsCAQAwTTEoMCYGA1UEChMfdGVjaCBDTj1TcG9rZS0wMiBDTj1jaXNj
byBDPWNvbTEhMB8GCSqGSIb3DQEJAhYSU3Bva2UtMDIuY2lzY28uY29tMIIBIjAN
BgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAmkLRbp+NTyQ5tiu6CgoHnkX+FdBH
RfIqzTY4pVG+AE6hMJe1d/jLVLBi6VLj8M32KcGsvQe7nyVt6iARyzcQuN3WVzQu
5D+kUSGZbrkI7ubrjiuMuSYeVrRSRM1YXrQ2znLzRc32+ShM3kkpsIUdif0i7+gk
SC3g+fdltqjQPRwHssdnofqS8jr7b282adTyT/RhG87rNRml8tf0GsNZ4DuXNrO0
4HPVUgsis8WCKQz5BdFA9N+IIbW0Qmwb8HyuQegukpKCeRpBzuf1UbZ9fjmRapMv
Bz7goopR3VosAQ0lgnHPrsezo6ADY5Lik7LOBE45IrnDatZsI5oS+GqvRQIDAQAB
oCEwHwYJKoZIhvcNAQkOMRIwEDAOBgNVHQ8BAf8EBAMCBaAwDQYJKoZIhvcNAQEF
BQADggEBAA7sht9FrIV77DvdXhOY3NUeZilDZDWvaKHRG0Ijjf+E2E/e+F9ifqzi
vqGEgF4mxyOYcccbDVyaFBtbA5SJtUOz4zkZZScB5JFIeBpIo+ggMsBjOXWRbvvH
h+GI2RgsuF9gz9jadbkNXOl7HJ/F2Lhvk8vufrLDYlw5X3qbk7QZLVXsoDeuPSSe
RXjz8cCQhLMIH22YkafdAch/ygfXdczHSlscYU9gV38NYlU9CIurEkVQ6lyE0IAb
FrBRaTQhGKBEXwbXFYuMumS/4dXhy/D75ou8mt2r3/sh60mJcRdgw/nqK+bxwX99
nDKt52mmas9FAuaar+6aWYA6YRiop9k=
---End - This line not part of the certificate request---
Redisplay enrollment request? [yes/no]: no
- CA签发证书
Hub-CA#crypto pki server ca request pkcs10 terminal
PKCS10 request in base64 or pem
% Enter Base64 encoded or PEM formatted PKCS10 enrollment request.
% End with a blank line or "quit" on a line by itself.
MIICszCCAZsCAQAwTTEoMCYGA1UEChMfdGVjaCBDTj1TcG9rZS0wMiBDTj1jaXNj
byBDPWNvbTEhMB8GCSqGSIb3DQEJAhYSU3Bva2UtMDIuY2lzY28uY29tMIIBIjAN
BgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAmkLRbp+NTyQ5tiu6CgoHnkX+FdBH
RfIqzTY4pVG+AE6hMJe1d/jLVLBi6VLj8M32KcGsvQe7nyVt6iARyzcQuN3WVzQu
5D+kUSGZbrkI7ubrjiuMuSYeVrRSRM1YXrQ2znLzRc32+ShM3kkpsIUdif0i7+gk
SC3g+fdltqjQPRwHssdnofqS8jr7b282adTyT/RhG87rNRml8tf0GsNZ4DuXNrO0
4HPVUgsis8WCKQz5BdFA9N+IIbW0Qmwb8HyuQegukpKCeRpBzuf1UbZ9fjmRapMv
Bz7goopR3VosAQ0lgnHPrsezo6ADY5Lik7LOBE45IrnDatZsI5oS+GqvRQIDAQAB
oCEwHwYJKoZIhvcNAQkOMRIwEDAOBgNVHQ8BAf8EBAMCBaAwDQYJKoZIhvcNAQEF
BQADggEBAA7sht9FrIV77DvdXhOY3NUeZilDZDWvaKHRG0Ijjf+E2E/e+F9ifqzi
vqGEgF4mxyOYcccbDVyaFBtbA5SJtUOz4zkZZScB5JFIeBpIo+ggMsBjOXWRbvvH
h+GI2RgsuF9gz9jadbkNXOl7HJ/F2Lhvk8vufrLDYlw5X3qbk7QZLVXsoDeuPSSe
RXjz8cCQhLMIH22YkafdAch/ygfXdczHSlscYU9gV38NYlU9CIurEkVQ6lyE0IAb
FrBRaTQhGKBEXwbXFYuMumS/4dXhy/D75ou8mt2r3/sh60mJcRdgw/nqK+bxwX99
nDKt52mmas9FAuaar+6aWYA6YRiop9k=
quit
% Enrollment request pending, reqId=3
Hub-CA#crypto pki server ca grant 3 # 颁发证书
% Granted certificate:
MIICtzCCAiCgAwIBAgIBBDANBgkqhkiG9w0BAQQFADAeMRwwGgYDVQQKExN0ZWNo
IENOPWNpc2NvIEM9Y29tMB4XDTIxMDEyNTA5MjIwOFoXDTIzMDExNTA5MjIwOFow
TTEoMCYGA1UEChMfdGVjaCBDTj1TcG9rZS0wMiBDTj1jaXNjbyBDPWNvbTEhMB8G
CSqGSIb3DQEJAhYSU3Bva2UtMDIuY2lzY28uY29tMIIBIjANBgkqhkiG9w0BAQEF
AAOCAQ8AMIIBCgKCAQEAmkLRbp+NTyQ5tiu6CgoHnkX+FdBHRfIqzTY4pVG+AE6h
MJe1d/jLVLBi6VLj8M32KcGsvQe7nyVt6iARyzcQuN3WVzQu5D+kUSGZbrkI7ubr
jiuMuSYeVrRSRM1YXrQ2znLzRc32+ShM3kkpsIUdif0i7+gkSC3g+fdltqjQPRwH
ssdnofqS8jr7b282adTyT/RhG87rNRml8tf0GsNZ4DuXNrO04HPVUgsis8WCKQz5
BdFA9N+IIbW0Qmwb8HyuQegukpKCeRpBzuf1UbZ9fjmRapMvBz7goopR3VosAQ0l
gnHPrsezo6ADY5Lik7LOBE45IrnDatZsI5oS+GqvRQIDAQABo1IwUDAOBgNVHQ8B
Af8EBAMCBaAwHwYDVR0jBBgwFoAUIeeFkyaiIRjw7j1oySP2EgU7ALcwHQYDVR0O
BBYEFLMxTTTNI7RYki1V3CIq6qMOUMr2MA0GCSqGSIb3DQEBBAUAA4GBABKmICQy
Xv21YUkt1Us7wQzrk5rmSMAJ8EpH28L8Hw0tEvrvKJJnCnLaRFID8hhgtRGQKaXA
3BbNuvPNAcz0bqiAoxU2n7YpSUBFLib2W5vVJ4rIiqy1XHK/fCUusPnq91KTBLE0
ooCkPi6nE49BgI6oovxUVgHuJRoHlH0SHp5s
- Spoke-02导入证书
Spoke-02(config)#crypto pki import dmvpn-cert certificate
Enter the base 64 encoded certificate.
End with a blank line or the word "quit" on a line by itself
MIICtzCCAiCgAwIBAgIBBDANBgkqhkiG9w0BAQQFADAeMRwwGgYDVQQKExN0ZWNo
IENOPWNpc2NvIEM9Y29tMB4XDTIxMDEyNTA5MjIwOFoXDTIzMDExNTA5MjIwOFow
TTEoMCYGA1UEChMfdGVjaCBDTj1TcG9rZS0wMiBDTj1jaXNjbyBDPWNvbTEhMB8G
CSqGSIb3DQEJAhYSU3Bva2UtMDIuY2lzY28uY29tMIIBIjANBgkqhkiG9w0BAQEF
AAOCAQ8AMIIBCgKCAQEAmkLRbp+NTyQ5tiu6CgoHnkX+FdBHRfIqzTY4pVG+AE6h
MJe1d/jLVLBi6VLj8M32KcGsvQe7nyVt6iARyzcQuN3WVzQu5D+kUSGZbrkI7ubr
jiuMuSYeVrRSRM1YXrQ2znLzRc32+ShM3kkpsIUdif0i7+gkSC3g+fdltqjQPRwH
ssdnofqS8jr7b282adTyT/RhG87rNRml8tf0GsNZ4DuXNrO04HPVUgsis8WCKQz5
BdFA9N+IIbW0Qmwb8HyuQegukpKCeRpBzuf1UbZ9fjmRapMvBz7goopR3VosAQ0l
gnHPrsezo6ADY5Lik7LOBE45IrnDatZsI5oS+GqvRQIDAQABo1IwUDAOBgNVHQ8B
Af8EBAMCBaAwHwYDVR0jBBgwFoAUIeeFkyaiIRjw7j1oySP2EgU7ALcwHQYDVR0O
BBYEFLMxTTTNI7RYki1V3CIq6qMOUMr2MA0GCSqGSIb3DQEBBAUAA4GBABKmICQy
Xv21YUkt1Us7wQzrk5rmSMAJ8EpH28L8Hw0tEvrvKJJnCnLaRFID8hhgtRGQKaXA
3BbNuvPNAcz0bqiAoxU2n7YpSUBFLib2W5vVJ4rIiqy1XHK/fCUusPnq91KTBLE0
ooCkPi6nE49BgI6oovxUVgHuJRoHlH0SHp5s
quit
% Router Certificate successfully imported
- 配置DMVPN环境
crypto isakmp enable
crypto isakmp policy 10
encr aes
hash sha256
authentication rsa-sig
lifetime 86400
group 2
crypto isakmp invalid-spi-recovery
crypto isakmp keepalive 30 10 periodic
crypto isakmp nat keepalive 360
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association replay disable
crypto ipsec transform-set 3DES esp-3des esp-sha-hmac
mode transport
crypto ipsec nat-transparency spi-matching
crypto ipsec profile NEPROF-MKT
set transform-set 3DES
set pfs group2
interface Tunnel20
description DMVPN-HUB
bandwidth 1000000
ip address 10.16.1.2 255.255.255.0
no ip redirects
ip mtu 1400
ip nhrp map 10.16.1.10 123.1.1.10
ip nhrp map multicast 123.1.1.10
ip nhrp nhs 10.16.1.10
ip nhrp authentication cisco
ip nhrp map multicast dynamic
ip nhrp network-id 20
ip nhrp holdtime 300
ip tcp adjust-mss 1360
ip ospf network broadcast
ip ospf priority 95
ip ospf cost 2000
load-interval 30
delay 1000
tunnel source Ethernet0/0
tunnel mode gre multipoint
tunnel key 20
tunnel path-mtu-discovery
tunnel bandwidth transmit 100000
tunnel bandwidth receive 100000
tunnel protection ipsec profile NEPROF-MKT
- 配置OSPF网络环境
interface Loopback0
ip address 192.168.2.1 255.255.255.0
ip ospf network point-to-point
ip ospf 100 area 2
router ospf 100
network 10.16.1.0 0.0.0.255 area 0
FlexVPN 中心转发实验
为了穿越NAT网络,所有spoke节点都与中心互连,所有流量都是通过中心转发,采用OSPF协议传递路由.
HUB节点配置
# IKEv2认证策略使用本地认证 ikev2 profile调用
aaa new-model
aaa authorization network IKEV2-VPN-AUTHOR-LIST local
# 客户端连接后推送IP地址 ikev2 profile调用
ip local pool IKEV2-VPN-ADDRESS-POOL 192.18.1.10 192.18.1.200
crypto ikev2 authorization policy IKEV2-VPN-AUTHOR-POLICY
pool IKEV2-VPN-ADDRESS-POOL
# 客户端合法的身份信息 ikev2 profile调用
crypto ikev2 keyring IKEV2-KEYRING
peer spoke-01
identity email spoke-01@newegg.org
pre-shared-key cisco
!
peer spoke-02
identity email spoke-02@newegg.org
pre-shared-key cisco
!
peer spoke-03
identity email spoke-03@newegg.org
pre-shared-key cisco
# 客户端认证的策略
crypto ikev2 profile IKEV2-VPN-PROFILE
match identity remote address 0.0.0.0
match identity remote email domain newegg.org
authentication remote pre-share
authentication local pre-share
# 客户端认证调用 IKEV2-KEYRING
keyring local IKEV2-KEYRING
# 授权客户端的认证方式和IP地址
aaa authorization group psk list IKEV2-VPN-AUTHOR-LIST IKEV2-VPN-AUTHOR-POLICY
# 调用虚模板
virtual-template 1
# IPSEC profile 虚拟接口调用
crypto ipsec profile IKEV2-IPSEC-PROFILE
# 调用IKEV2的profile
set ikev2-profile IKEV2-VPN-PROFILE
interface Loopback0
ip ospf 1 area 0
interface Virtual-Template1 type tunnel
ip unnumbered Loopback0
ip mtu 1400
ip ospf 1 area 0
tunnel mode ipsec ipv4
tunnel protection ipsec profile IKEV2-IPSEC-PROFILE
router ospf 1
router-id 192.168.10.1
Spoke-01至03的 配置
aaa new-model
aaa authorization network IKEV2-VPN-AUTHOR-LIST local
# 模拟使用DNS的场景,动态IP或者静态IP都可以使用.
ip host hub.newegg.org 123.1.1.10
ip name-server 123.1.1.10
crypto ikev2 authorization policy IKEV2-VPN-AUTHOR-POLICY
# 定义HUB的身份信息
crypto ikev2 keyring IKEV2-KEYRING
peer hub
address 0.0.0.0 0.0.0.0
pre-shared-key local cisco
pre-shared-key remote cisco
crypto ikev2 profile IKEV2-VPN-PROFILE
match identity remote address 0.0.0.0
# 定义自己的身份信息每个spoke需要修改 spoke-01@newegg.org
identity local email spoke-01@newegg.org
authentication remote pre-share
authentication local pre-share
keyring local IKEV2-KEYRING
aaa authorization group psk list IKEV2-VPN-AUTHOR-LIST IKEV2-VPN-AUTHOR-POLICY
crypto ipsec profile IKEV2-IPSEC-PROFILE
set ikev2-profile IKEV2-VPN-PROFILE
interface Loopback0
ip ospf 1 area 0
interface Tunnel0
# IP地址中心下发
ip address negotiated
ip mtu 1400
ip ospf 1 area 0
tunnel source Ethernet0/0
tunnel mode ipsec ipv4
tunnel destination dynamic
tunnel protection ipsec profile IKEV2-IPSEC-PROFILE
# OSPF 配置 每个spoke需要修改route id
router ospf 1
router-id 192.168.1.1
# 启用FlexVPN
crypto ikev2 client flexvpn IKEV2-FLEX-CLIENT
peer 1 fqdn hub.newegg.org dynamic
client connect Tunnel0
HUB验证
VPN状态验证
Hub-CA#show crypto ikev2 sa
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
3 123.1.1.10/500 123.1.1.2/500 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA512, Hash: SHA512, DH Grp:5, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/2010 sec
Tunnel-id Local Remote fvrf/ivrf Status
1 123.1.1.10/500 123.1.1.1/500 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA512, Hash: SHA512, DH Grp:5, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/2127 sec
Tunnel-id Local Remote fvrf/ivrf Status
2 123.1.1.10/4500 123.1.1.3/4500 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA512, Hash: SHA512, DH Grp:5, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/2215 sec
IPv6 Crypto IKEv2 SA
OSPF状态验证
Hub-CA#show ip os neighbor
Neighbor ID Pri State Dead Time Address Interface
192.168.2.1 0 FULL/ - 00:00:31 192.18.1.15 Virtual-Access3
192.168.1.1 0 FULL/ - 00:00:30 192.18.1.14 Virtual-Access2
192.168.3.1 0 FULL/ - 00:00:34 192.18.1.13 Virtual-Access1
Spoke验证
VPN状态验证
- Spoke-01
Spoke-01#show crypto ikev2 sa
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
1 123.1.1.1/500 123.1.1.10/500 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA512, Hash: SHA512, DH Grp:5, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/2270 sec
IPv6 Crypto IKEv2 SA
- Spoke-02
Spoke-02#show crypto ikev2 sa
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
1 123.1.1.2/500 123.1.1.10/500 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA512, Hash: SHA512, DH Grp:5, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/2197 sec
IPv6 Crypto IKEv2 SA
- Spoke-03
Spoke-03#show crypto ikev2 sa
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
1 172.16.168.2/4500 123.1.1.10/4500 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA512, Hash: SHA512, DH Grp:5, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/2304 sec
IPv6 Crypto IKEv2 SA
OSPF状态验证
- Spoke-01
Spoke-01#show ip os neighbor
Neighbor ID Pri State Dead Time Address Interface
192.168.10.1 0 FULL/ - 00:00:33 192.168.10.1 Tunnel0
Spoke-01#show ip route ospf
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
a - application route
+ - replicated route, % - next hop override
Gateway of last resort is not set
192.18.1.0/32 is subnetted, 3 subnets
O 192.18.1.13 [110/3000] via 192.168.10.1, 00:39:48, Tunnel0
O 192.18.1.15 [110/3000] via 192.168.10.1, 00:37:50, Tunnel0
192.168.2.0/32 is subnetted, 1 subnets
O 192.168.2.1 [110/2001] via 192.168.10.1, 00:37:34, Tunnel0
192.168.3.0/32 is subnetted, 1 subnets
O 192.168.3.1 [110/2001] via 192.168.10.1, 00:39:48, Tunnel0
192.168.10.0/32 is subnetted, 1 subnets
O 192.168.10.1 [110/1001] via 192.168.10.1, 00:39:48, Tunnel0
- Spoke-02
Spoke-02#show ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
192.168.10.1 0 FULL/ - 00:00:35 192.168.10.1 Tunnel0
Spoke-02#show ip route ospf
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
a - application route
+ - replicated route, % - next hop override
Gateway of last resort is not set
192.18.1.0/32 is subnetted, 3 subnets
O 192.18.1.13 [110/3000] via 192.168.10.1, 00:38:16, Tunnel0
O 192.18.1.14 [110/3000] via 192.168.10.1, 00:38:16, Tunnel0
192.168.1.0/32 is subnetted, 1 subnets
O 192.168.1.1 [110/2001] via 192.168.10.1, 00:38:16, Tunnel0
192.168.3.0/32 is subnetted, 1 subnets
O 192.168.3.1 [110/2001] via 192.168.10.1, 00:38:16, Tunnel0
192.168.10.0/32 is subnetted, 1 subnets
O 192.168.10.1 [110/1001] via 192.168.10.1, 00:38:16, Tunnel0
- Spoke-03
Spoke-03#show ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
192.168.10.1 0 FULL/ - 00:00:31 192.168.10.1 Tunnel0
Spoke-03#show ip route ospf
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
a - application route
+ - replicated route, % - next hop override
Gateway of last resort is 172.16.168.1 to network 0.0.0.0
192.18.1.0/32 is subnetted, 3 subnets
O 192.18.1.14 [110/3000] via 192.168.10.1, 00:40:32, Tunnel0
O 192.18.1.15 [110/3000] via 192.168.10.1, 00:38:44, Tunnel0
192.168.1.0/32 is subnetted, 1 subnets
O 192.168.1.1 [110/2001] via 192.168.10.1, 00:40:32, Tunnel0
192.168.2.0/32 is subnetted, 1 subnets
O 192.168.2.1 [110/2001] via 192.168.10.1, 00:38:29, Tunnel0
192.168.10.0/32 is subnetted, 1 subnets
O 192.168.10.1 [110/1001] via 192.168.10.1, 00:42:10, Tunnel0
FlexVPN 中心转发(双中心)
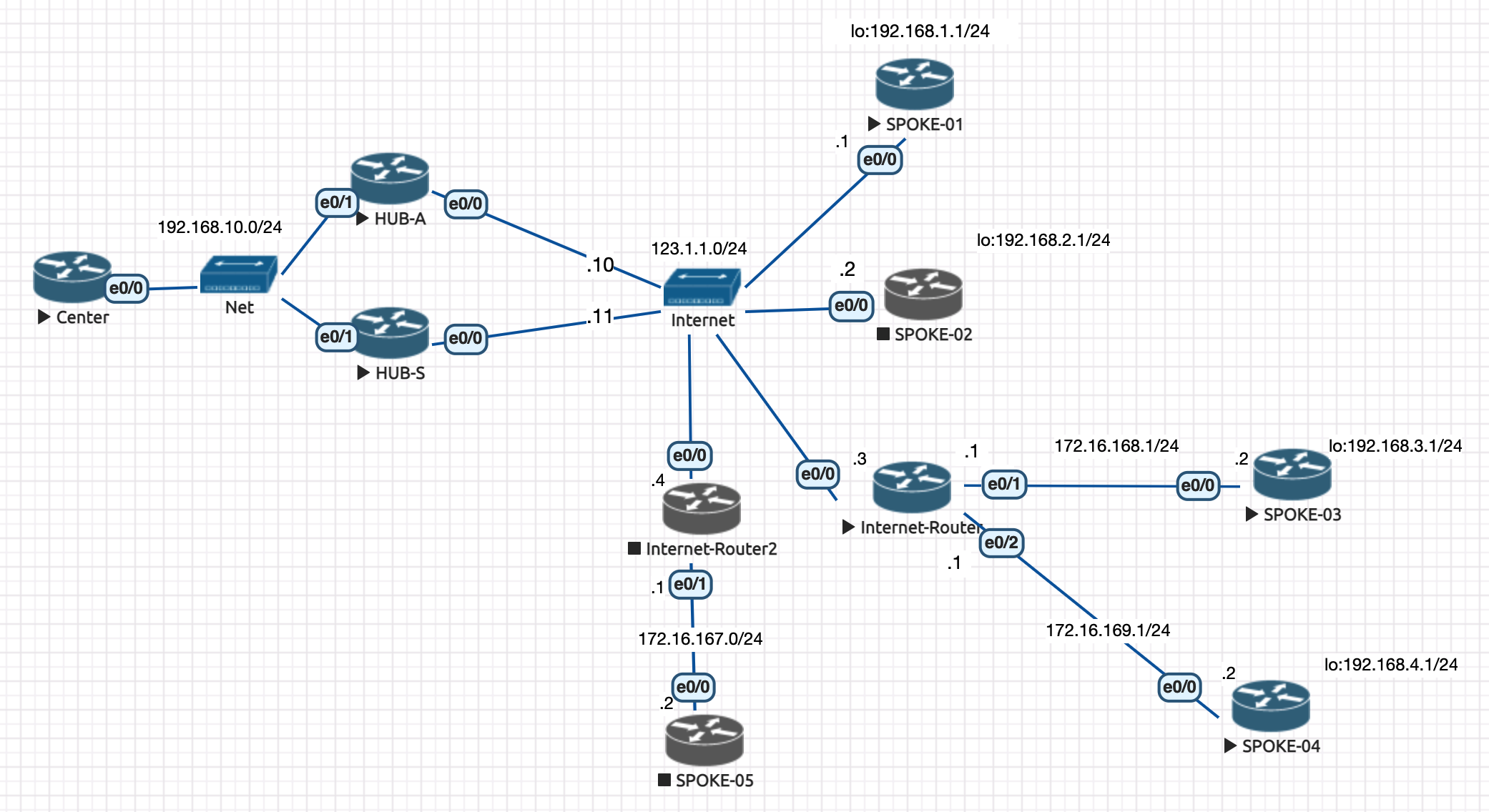
网络拓结构为下图:
HUB-A节点配置
# 基础配置
interface Loopback0
ip address 192.168.20.10 255.255.255.255
# IKEV2 LB配置
interface Ethernet0/1
ip address 192.168.10.10 255.255.255.0
standby 1 ip 192.168.10.1
standby 1 priority 105
standby 1 preempt
standby 1 name ikev2LB
# IKEv2认证策略使用本地认证 ikev2 profile调用
aaa new-model
aaa authorization network IKEV2-VPN-AUTHOR-LIST local
# 客户端连接后推送IP地址 ikev2 profile调用
ip local pool IKEV2-VPN-ADDRESS-POOL 192.18.1.10 192.18.1.200
crypto ikev2 authorization policy IKEV2-VPN-AUTHOR-POLICY
pool IKEV2-VPN-ADDRESS-POOL
# 客户端合法的身份信息 ikev2 profile调用
crypto ikev2 keyring IKEV2-KEYRING
peer spoke-01
identity email spoke-01@newegg.org
pre-shared-key cisco
!
peer spoke-02
identity email spoke-02@newegg.org
pre-shared-key cisco
!
peer spoke-03
identity email spoke-03@newegg.org
pre-shared-key cisco
!
peer spoke-04
identity email spoke-04@newegg.org
pre-shared-key cisco
# 客户端认证的策略
crypto ikev2 profile IKEV2-VPN-PROFILE
match identity remote address 0.0.0.0
match identity remote email domain newegg.org
authentication remote pre-share
authentication local pre-share
# 客户端死亡检测
dpd 30 2 periodic
# 客户端认证调用 IKEV2-KEYRING
keyring local IKEV2-KEYRING
# 授权客户端的认证方式和IP地址
aaa authorization group psk list IKEV2-VPN-AUTHOR-LIST IKEV2-VPN-AUTHOR-POLICY
# 调用虚模板
virtual-template 1
# IPSEC profile 虚拟接口调用
crypto ipsec profile IKEV2-IPSEC-PROFILE
# 调用IKEV2的profile
set ikev2-profile IKEV2-VPN-PROFILE
interface Virtual-Template1 type tunnel
ip unnumbered Loopback0
ip mtu 1400
ip ospf 1 area 0
tunnel mode ipsec ipv4
tunnel protection ipsec profile IKEV2-IPSEC-PROFILE
router ospf 1
network 192.168.10.0 0.0.0.255 area 0
router-id 192.168.10.10
HUB-S节点配置
# 基础配置
interface Loopback0
ip address 192.168.20.11 255.255.255.255
# IKEV2 LB配置
interface Ethernet0/1
ip address 192.168.10.11 255.255.255.0
standby 1 ip 192.168.10.1
standby 1 priority 110
standby 1 preempt
standby 1 name ikev2LB
# IKEv2认证策略使用本地认证 ikev2 profile调用
aaa new-model
aaa authorization network IKEV2-VPN-AUTHOR-LIST local
# 客户端连接后推送IP地址 ikev2 profile调用
ip local pool IKEV2-VPN-ADDRESS-POOL 192.19.1.10 192.19.1.200
crypto ikev2 authorization policy IKEV2-VPN-AUTHOR-POLICY
pool IKEV2-VPN-ADDRESS-POOL
# 客户端合法的身份信息 ikev2 profile调用
crypto ikev2 keyring IKEV2-KEYRING
peer spoke-01
identity email spoke-01@newegg.org
pre-shared-key cisco
!
peer spoke-02
identity email spoke-02@newegg.org
pre-shared-key cisco
!
peer spoke-03
identity email spoke-03@newegg.org
pre-shared-key cisco
!
peer spoke-04
identity email spoke-04@newegg.org
pre-shared-key cisco
# 客户端认证的策略
crypto ikev2 profile IKEV2-VPN-PROFILE
match identity remote address 0.0.0.0
match identity remote email domain newegg.org
authentication remote pre-share
authentication local pre-share
# 客户端死亡检测
dpd 30 2 periodic
# 客户端认证调用 IKEV2-KEYRING
keyring local IKEV2-KEYRING
# 授权客户端的认证方式和IP地址
aaa authorization group psk list IKEV2-VPN-AUTHOR-LIST IKEV2-VPN-AUTHOR-POLICY
# 调用虚模板
virtual-template 1
# IPSEC profile 虚拟接口调用
crypto ipsec profile IKEV2-IPSEC-PROFILE
# 调用IKEV2的profile
set ikev2-profile IKEV2-VPN-PROFILE
interface Virtual-Template1 type tunnel
ip unnumbered Loopback0
ip mtu 1400
ip ospf 1 area 0
tunnel mode ipsec ipv4
tunnel protection ipsec profile IKEV2-IPSEC-PROFILE
router ospf 1
network 192.168.10.0 0.0.0.255 area 0
router-id 192.168.10.11
Spoke配置模板
!
aaa new-model
!
aaa authorization network IKEV2-VPN-AUTHOR-LIST local
!
ip host hub1.newegg.org 123.1.1.10
ip host hub2.newegg.org 123.1.1.11
ip name-server 123.1.1.10
!
crypto ikev2 authorization policy IKEV2-VPN-AUTHOR-POLICY
!
crypto ikev2 keyring IKEV2-KEYRING
peer hub
address 0.0.0.0 0.0.0.0
pre-shared-key local cisco
pre-shared-key remote cisco
!
crypto ikev2 profile IKEV2-VPN-PROFILE
match identity remote address 0.0.0.0
# 注意修改自己的身份信息
identity local email spoke-04@newegg.org
authentication remote pre-share
authentication local pre-share
keyring local IKEV2-KEYRING
dpd 30 2 periodic
aaa authorization group psk list IKEV2-VPN-AUTHOR-LIST IKEV2-VPN-AUTHOR-POLICY
!
!
crypto ipsec profile IKEV2-IPSEC-PROFILE
set ikev2-profile IKEV2-VPN-PROFILE
!
interface Loopback0
ip ospf 1 area 0
!
interface Tunnel0
ip address negotiated
ip mtu 1400
ip ospf 1 area 0
tunnel source Ethernet0/0
tunnel mode ipsec ipv4
tunnel destination dynamic
tunnel protection ipsec profile IKEV2-IPSEC-PROFILE
!
router ospf 1
# 注意修改自己的身份信息
router-id 192.168.3.1
!
# 切换HUB的sla检测配置
ip sla 10
icmp-echo 123.1.1.10
ip sla schedule 10 life forever start-time now
ip sla 11
icmp-echo 123.1.1.11
ip sla schedule 11 life forever start-time now
!
track 10 ip sla 10 reachability
!
track 11 ip sla 11 reachability
!
# track 10 检测到故障后切换HUB
crypto ikev2 client flexvpn IKEV2-FLEX-CLIENT
peer 1 fqdn hub1.newegg.org dynamic track 10
peer 2 fqdn hub2.newegg.org dynamic track 11
peer reactivate
client connect Tunnel0
!
FlexVPN 中心转发(双中心PKI认证)
HUB节点配置模板
aaa new-model
!
aaa authorization network IKEV2-VPN-AUTHOR-LIST local
! 证书导入参考PKI认证试验环节的证书申请以及导入.
crypto pki trustpoint Hub-A
enrollment terminal
subject-name cn=test,dc=buyabs,dc=corp
revocation-check none
rsakeypair hub-key
!
crypto pki certificate map IKEV2-VPN-PKI-MAP 10
subject-name co buyabs
! 证书导入参考PKI认证试验环节的证书申请以及导入.
crypto pki certificate chain Hub-A
certificate 550000001040B74575AEB9BFFC000000000010
..........
quit
certificate ca 5D26D6DD736439B14C669C70A1C04C97
..........
quit
!
crypto ikev2 authorization policy IKEV2-VPN-AUTHOR-POLICY
pool IKEV2-VPN-ADDRESS-POOL
!
crypto ikev2 proposal IKEV2-VPN-PROPOSAL
encryption 3des
integrity sha1
group 2
!
crypto ikev2 policy IKEV2-VPN-POLICY
proposal IKEV2-VPN-PROPOSAL
!
crypto ikev2 profile IKEV2-VPN-PROFILE
match certificate IKEV2-VPN-PKI-MAP
identity local dn
authentication remote rsa-sig
authentication local rsa-sig
pki trustpoint Hub-A
dpd 30 2 periodic
aaa authorization group cert list IKEV2-VPN-AUTHOR-LIST IKEV2-VPN-AUTHOR-POLICY
virtual-template 1
!
crypto ipsec profile IKEV2-IPSEC-PROFILE
set ikev2-profile IKEV2-VPN-PROFILE
!
interface Virtual-Template1 type tunnel
ip unnumbered Loopback0
ip mtu 1400
ip ospf 1 area 0
tunnel mode ipsec ipv4
tunnel protection ipsec profile IKEV2-IPSEC-PROFILE
!
router ospf 1
network 192.168.10.0 0.0.0.255 area 0
!
ip local pool IKEV2-VPN-ADDRESS-POOL 192.18.1.10 192.18.1.200
Spoke节点配置模板
! 证书导入参考PKI认证试验环节的证书申请以及导入.
crypto pki trustpoint Spoke-01
enrollment terminal
subject-name cn=test1,dc=buyabs,dc=corp
revocation-check none
rsakeypair spoke-key
!
crypto pki certificate map IKEV2-VPN-PKI-MAP 10
subject-name co buyabs
!
! 证书导入参考PKI认证试验环节的证书申请以及导入.
crypto pki certificate chain Spoke-01
certificate 55000000121684B2BE474DFD35000000000012
...........
quit
certificate ca 5D26D6DD736439B14C669C70A1C04C97
...........
quit
!
ip sla 10
icmp-echo 123.1.1.10
ip sla schedule 10 life forever start-time now
ip sla 11
icmp-echo 123.1.1.11
ip sla schedule 11 life forever start-time now
!
track 10 ip sla 10 reachability
!
track 11 ip sla 11 reachability
!
crypto ikev2 proposal IKEV2-VPN-PROPOSAL
encryption 3des
integrity sha1
group 2
!
crypto ikev2 policy IKEV2-VPN-POLICY
proposal IKEV2-VPN-PROPOSAL
!
crypto ikev2 profile IKEV2-VPN-PROFILE
match certificate IKEV2-VPN-PKI-MAP
identity local dn
authentication remote rsa-sig
authentication local rsa-sig
pki trustpoint Spoke-01
dpd 30 2 periodic
!
crypto ikev2 client flexvpn IKEV2-FLEX-CLIENT
peer 1 fqdn hub1.newegg.org dynamic track 10
peer 2 fqdn hub2.newegg.org dynamic track 11
peer reactivate
client connect Tunnel0
!
crypto ipsec profile IKEV2-IPSEC-PROFILE
set ikev2-profile IKEV2-VPN-PROFILE
!
interface Tunnel0
ip address negotiated
ip mtu 1400
ip ospf 1 area 0
tunnel source Ethernet0/0
tunnel mode ipsec ipv4
tunnel destination dynamic
tunnel protection ipsec profile IKEV2-IPSEC-PROFILE
!
验证
Spoke-01#show crypto ikev2 session
IPv4 Crypto IKEv2 Session
Session-id:53, Status:UP-ACTIVE, IKE count:1, CHILD count:1
Tunnel-id Local Remote fvrf/ivrf Status
1 123.1.1.1/500 123.1.1.10/500 none/none READY
Encr: 3DES, PRF: SHA1, Hash: SHA96, DH Grp:2, Auth sign: RSA, Auth verify: RSA
Life/Active Time: 86400/57 sec
Child sa: local selector 0.0.0.0/0 - 255.255.255.255/65535
remote selector 0.0.0.0/0 - 255.255.255.255/65535
ESP spi in/out: 0x4E79702B/0xAC42F888
IPv6 Crypto IKEv2 Session
Spoke-01#show crypto ikev2 sa detailed
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
1 123.1.1.1/500 123.1.1.10/500 none/none READY
Encr: 3DES, PRF: SHA1, Hash: SHA96, DH Grp:2, Auth sign: RSA, Auth verify: RSA
Life/Active Time: 86400/69 sec
CE id: 1085, Session-id: 53
Status Description: Negotiation done
Local spi: 9806C3226E59BA10 Remote spi: 25D995B89823CFBC
Local id: cn=test1,dc=buyabs,dc=corp
Remote id: cn=test,dc=buyabs,dc=corp
Local req msg id: 4 Remote req msg id: 2
Local next msg id: 4 Remote next msg id: 2
Local req queued: 4 Remote req queued: 2
Local window: 5 Remote window: 5
DPD configured for 30 seconds, retry 2
Fragmentation not configured.
Extended Authentication not configured.
NAT-T is not detected
Cisco Trust Security SGT is disabled
Initiator of SA : Yes
Pushed IP address: 192.18.1.32
IPv6 Crypto IKEv2 SA
Debug
# The router debugs for tunnel negotiation are:
debug crypto ikev2
debug crypto ikev2 error
debug crypto ikev2 internal
# The router debugs for certificate authentication are:
debug cry pki validation
debug cry pki transaction
debug cry pki messages
FlexVPN 实现Spoke访问Spoke
本实验实现spoke之间互访的时候不通过中心转发包括spoke在PAT之后.
HUB节点配置
注意Virtual-Template接口的mode和中心转发的mode为 gre ip.ipsec transform-set为transport.
aaa new-model
!
!
aaa authorization network IKEV2-VPN-AUTHOR-LIST local
!
crypto ikev2 authorization policy IKEV2-VPN-AUTHOR-POLICY
pool IKEV2-VPN-ADDRESS-POOL
!
crypto ikev2 keyring IKEV2-KEYRING
peer spoke
identity email domain newegg.org
pre-shared-key cisco
!
crypto ikev2 profile IKEV2-VPN-PROFILE
match identity remote address 0.0.0.0
match identity remote email domain newegg.org
identity local email hub@newegg.org
authentication remote pre-share
authentication local pre-share
keyring local IKEV2-KEYRING
aaa authorization group psk list IKEV2-VPN-AUTHOR-LIST IKEV2-VPN-AUTHOR-POLICY
virtual-template 1
!
crypto ipsec transform-set IKEV2-VPN-IPSET-SET esp-3des esp-md5-hmac
mode transport
!
crypto ipsec profile IKEV2-IPSEC-PROFILE
set transform-set IKEV2-VPN-IPSET-SET
set ikev2-profile IKEV2-VPN-PROFILE
!
interface Loopback0
ip ospf 1 area 0
!
interface Virtual-Template1 type tunnel
ip unnumbered Loopback0
ip mtu 1400
ip nhrp network-id 1
ip nhrp redirect
ip ospf 1 area 0
tunnel protection ipsec profile IKEV2-IPSEC-PROFILE
!
router ospf 1
router-id 192.168.10.1
!
ip local pool IKEV2-VPN-ADDRESS-POOL 192.18.1.10 192.18.1.200
Spoke-01至03的 配置
注意tunnel接口的mode和中心转发的mode为 gre ip.ipsec transform-set为transport.
aaa new-model
!
aaa authorization network IKEV2-VPN-AUTHOR-LIST local
!
crypto ikev2 authorization policy IKEV2-VPN-AUTHOR-POLICY
!
crypto ikev2 keyring IKEV2-KEYRING
peer newegg
address 0.0.0.0 0.0.0.0
identity email domain newegg.org
pre-shared-key cisco
!
!
!
crypto ikev2 profile IKEV2-VPN-PROFILE
match identity remote address 0.0.0.0
match identity remote email domain newegg.org
identity local email spoke-01@newegg.org
authentication remote pre-share
authentication local pre-share
keyring local IKEV2-KEYRING
aaa authorization group psk list IKEV2-VPN-AUTHOR-LIST IKEV2-VPN-AUTHOR-POLICY
virtual-template 1
!
!
crypto ipsec transform-set IKEV2-VPN-IPSET-SET esp-3des esp-md5-hmac
mode transport
!
crypto ipsec profile IKEV2-IPSEC-PROFILE
set transform-set IKEV2-VPN-IPSET-SET
set ikev2-profile IKEV2-VPN-PROFILE
!
interface Loopback0
ip ospf 1 area 0
!
interface Tunnel0
ip address negotiated
ip mtu 1400
ip nhrp network-id 1
ip nhrp shortcut virtual-template 1
ip ospf 1 area 0
tunnel source Ethernet0/0
tunnel destination 123.1.1.10
tunnel protection ipsec profile IKEV2-IPSEC-PROFILE
!
interface Virtual-Template1 type tunnel
ip unnumbered Loopback0
ip mtu 1400
ip nhrp network-id 1
ip nhrp shortcut virtual-template 1
ip ospf 1 area 0
tunnel source Ethernet0/0
tunnel destination 123.1.1.10
tunnel protection ipsec profile IKEV2-IPSEC-PROFILE
!
router ospf 1
router-id 192.168.1.1
HUB 验证
Hub-CA#show ip os neighbor
Neighbor ID Pri State Dead Time Address Interface
192.168.1.1 0 FULL/ - 00:00:35 192.18.1.78 Virtual-Access1
192.168.2.1 0 FULL/ - 00:00:31 192.18.1.77 Virtual-Access2
VPN状态验证
Hub-CA#show crypto ikev2 sa
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
2 123.1.1.10/500 123.1.1.1/500 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA512, Hash: SHA512, DH Grp:5, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/1087 sec
Tunnel-id Local Remote fvrf/ivrf Status
1 123.1.1.10/500 123.1.1.2/500 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA512, Hash: SHA512, DH Grp:5, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/1108 sec
IPv6 Crypto IKEv2 SA
OSPF状态验证
Hub-CA#show ip os neighbor
Neighbor ID Pri State Dead Time Address Interface
192.168.1.1 0 FULL/ - 00:00:35 192.18.1.78 Virtual-Access1
192.168.2.1 0 FULL/ - 00:00:39 192.18.1.77 Virtual-Access2
Spoke验证
VPN状态验证
Spoke-01#show crypto ikev2 sa
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
3 123.1.1.1/500 123.1.1.2/500 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA512, Hash: SHA512, DH Grp:5, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/1145 sec
Tunnel-id Local Remote fvrf/ivrf Status
1 123.1.1.1/500 123.1.1.10/500 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA512, Hash: SHA512, DH Grp:5, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/1181 sec
IPv6 Crypto IKEv2 SA
OSPF状态验证
Spoke-01#show ip os neighbor
Neighbor ID Pri State Dead Time Address Interface
192.168.2.1 0 FULL/ - 00:00:36 192.168.2.1 Virtual-Access1
192.168.10.1 0 FULL/ - 00:00:33 192.168.10.1 Tunnel0
NHRP状态验证
Spoke-01#show ip nhrp
192.18.1.77/32 via 192.18.1.77
Virtual-Access1 created 00:18:35, expire 01:41:25
Type: dynamic, Flags: router nhop rib nho
NBMA address: 123.1.1.2
192.168.1.1/32 via 192.18.1.78
Virtual-Access1 created 00:18:35, expire 01:41:26
Type: dynamic, Flags: router unique local
NBMA address: 123.1.1.1
(no-socket)
192.168.2.1/32 via 192.18.1.77
Virtual-Access1 created 00:18:34, expire 01:41:25
Type: dynamic, Flags: router rib nho
NBMA address: 123.1.1.2
PAT之后的SPOKE状态
Spoke-03#show crypto session
Crypto session current status
Interface: Tunnel0
Profile: IKEV2-VPN-PROFILE
Session status: UP-ACTIVE
Peer: 123.1.1.10 port 4500
Session ID: 1
IKEv2 SA: local 172.16.168.2/4500 remote 123.1.1.10/4500 Active
IPSEC FLOW: permit 47 host 172.16.168.2 host 123.1.1.10
Active SAs: 2, origin: crypto map
Interface: Virtual-Access1
Profile: IKEV2-VPN-PROFILE
Session status: UP-ACTIVE
Peer: 123.1.1.1 port 4500
Session ID: 2
IKEv2 SA: local 172.16.168.2/4500 remote 123.1.1.1/4500 Active
IPSEC FLOW: permit 47 host 172.16.168.2 host 123.1.1.1
Active SAs: 4, origin: crypto map
Interface: Virtual-Access2
Profile: IKEV2-VPN-PROFILE
Session status: UP-ACTIVE
Peer: 123.1.1.2 port 4500
Session ID: 3
IKEv2 SA: local 172.16.168.2/4500 remote 123.1.1.2/4500 Active
IPSEC FLOW: permit 47 host 172.16.168.2 host 123.1.1.2
Active SAs: 4, origin: crypto map
Spoke-03#show ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
192.168.2.1 0 FULL/ - 00:00:32 192.168.2.1 Virtual-Access2
192.168.1.1 0 FULL/ - 00:00:31 192.168.1.1 Virtual-Access1
192.168.10.1 0 FULL/ - 00:00:33 192.168.10.1 Tunnel0
Spoke-03#show crypto ikev2 sa
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
3 172.16.168.2/4500 123.1.1.2/4500 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA512, Hash: SHA512, DH Grp:5, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/283 sec
Tunnel-id Local Remote fvrf/ivrf Status
1 172.16.168.2/4500 123.1.1.10/4500 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA512, Hash: SHA512, DH Grp:5, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/588 sec
Tunnel-id Local Remote fvrf/ivrf Status
2 172.16.168.2/4500 123.1.1.1/4500 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA512, Hash: SHA512, DH Grp:5, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/287 sec
IPv6 Crypto IKEv2 SA










评论抢沙发